Google is one of the most famous search engines in the world. However, searching Google is an art that many people don’t quite understand. And a case apart are those who prefer to ask you rather than do a simple google search. Luckily, there are awareness pages like lmgtfy Do you want to know how to be a hacker? Here’s the link: http://lmgtfy.com/?q=how+to+be+a+hackerhttp://lmgtfy.com/?q=As+ser+hacker
But in this article we will go further. Google has advanced search options: the so-called Google Dorks. Here I’ll explain each of the different dorks that exist, and show you some examples of how you can discover sensitive information and find pages and files of a target through Google Dorks.
Types of Google Dorks
| Dork | Descripción |
|---|---|
| “t1 t2” | Forces the terms t1 and t2 to appear in sequence. |
| t1 AND t2 | Displays pages containing the terms t1 and t2. |
| t1 OR t2 | Displays pages that contain t1 and pages that contain t2. |
| +t1 | Forces t1 to appear. |
| -t1 | Excludes pages containing t1 from the results. |
| intitle:t1 | t1 appears in the html title tag or by the page. |
| allintitle:t1 t2 | Both t1 and t2 appear in the title tag. Cannot be used with other operators. |
| allintext:t1 | Searches for t1 in the text of the page (anywhere except the title, URL and links). Cannot be used with other operators |
| inurl:t1 | Searches for t1 in the URL or by page. |
| allinurl: t1 t2 | Look for t1 and t2 only in the URL (Must be both). Cannot be used with other operators. |
| site:t1 | Searches only in the t1 domain or its subdomains |
| filetype:t1 | Search for files with extension t1 |
| link:t1 | Look for pages with links to t1. t1 must be a domain. |
| inanchor: t1 | Look for links to t1, even if those links do not refer to anything related to t1. |
| cache:t1 | Displays the google cached content of t1. t1 must be a domain/url, and cannot be used with other operators. |
| numrange: t1-t2 | Look for a range number t1-t2 |
| daterange:date1 – date2 | Search pages published between date1 and date2. Dates must be in Julian format. |
| &as_qdr=m3 | This dork has to be put in the url. Displays pages updated 3 months or less ago. |
| &as_qdr=3m | As above, but with pages that have not been updated for 3 months or more. |
| info:t1 | Displays a summary result on t1. t1 must be a domain/url. |
Google Hacking
Now let’s see some tricks to take advantage of these dorks in the face of ethical hacking.
Google Cache
You can use google’s cache to view a website anonymously. That way, you can crawl the entire web without sending a single package to that domain.
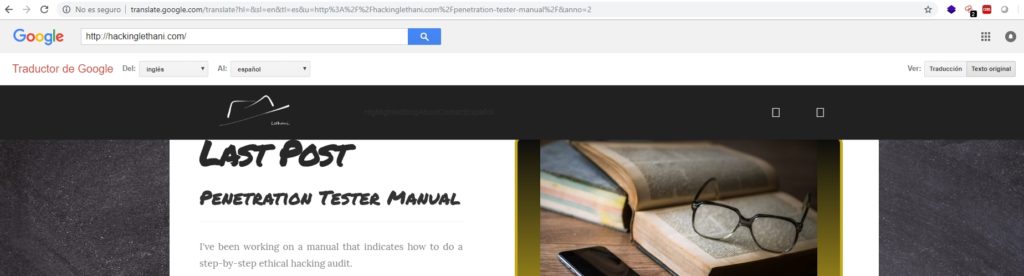
Proxy
You can also crawl anonymously using google’s online web page translator. Translate into any language and then select “orignal text” and you will be able to browse the page using google as a proxy.
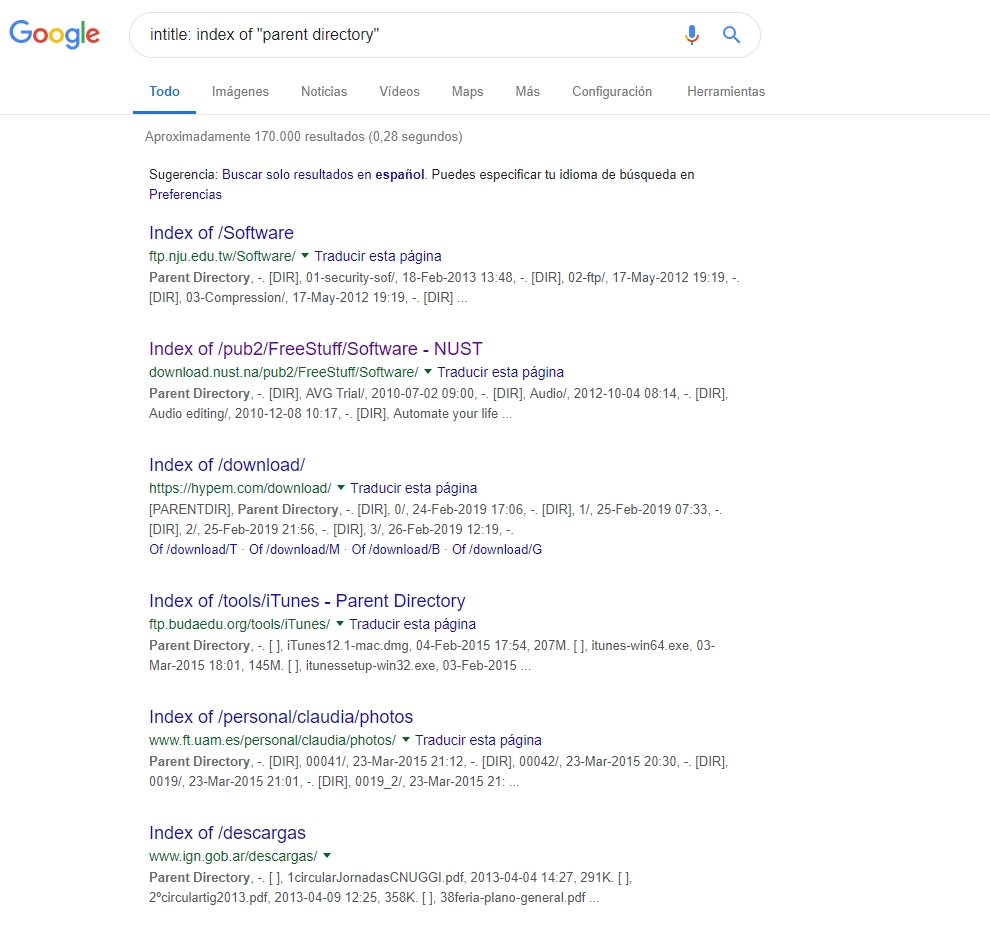
Directory Listening
Finding a directory listening is something very interesting when auditing, since in them you can find files with sensitive information. Through google dorks you can find directory listenings indexed in google that otherwise would go unnoticed. Let’s see some examples:
- intitle: index of “parent directory”
- intitle: index of name size
- intitle:index.of.admin
- inttitle:index.of inurl:admin
- filetype:log inurl:ws_ftp log
- intitle:index.of “server at”
- intitle:index.of “Apache/1.3.27 Server at”
If you want to search directory listenings of a specific domain, just concatenate the previous dorks with site:[domain].
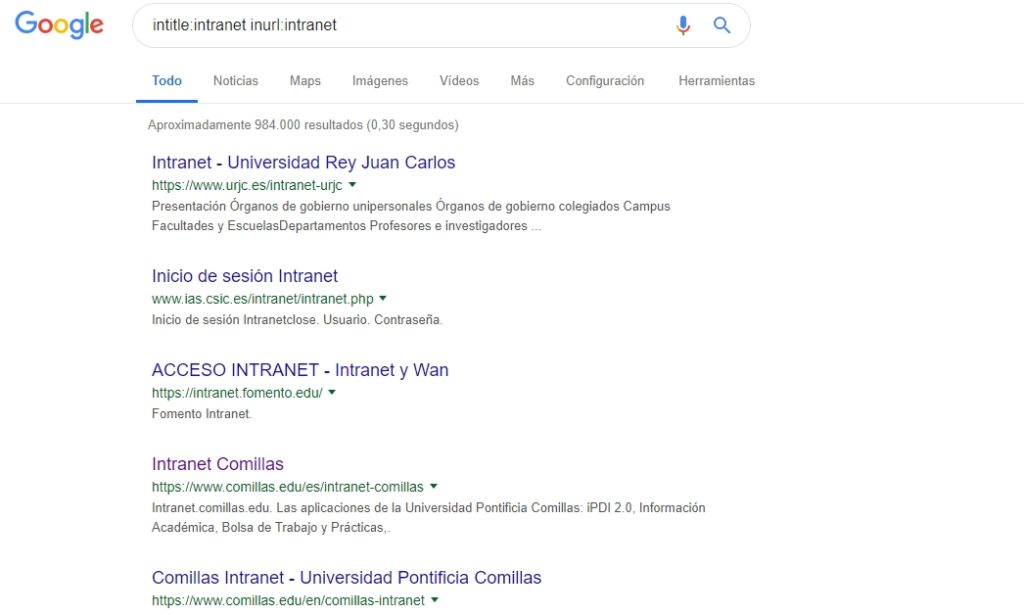
Intranets
It is possible that a corporation’s internal network is misconfigured and can be accessed from outside. If so, and google has indexed it, you can discover intranets using the following google dorks:
- intitle:intranet
- inurl:intranet
- intext:”human resources”
- intranet | help.desk
- “help.desk” | help.desk
E-mails
You can find emails with which you can later perform social engineering using the following dork:
“@gmail.com” -www.gmail.com
With this dork you would get the gmail accounts (change it to get accounts from another host).
Site crawling
Finally, here you can find a list of interesting crawling dorks. To exemplify, I will assume that we want to find out information from hackinglethani.com:
| Dork | Descripción |
|---|---|
| site:hackinglethani.com -www.hackinglethani.com | Used to find subdomains. |
| site:hackinglethani.com intitle:error|warning | To search for error pages. |
| site:hackinglethani.com login|logon | To search for logins. |
| site:hackinglethani.com admin|administrator | To search for administration pages. |
| site:hackinglethani.com inurl:temp | inurl:backup | inurl:bak | To search for backups and temporary files. |
| site:hackinglethani.com -ext:html | Displays all files in the domain except those with an html extension. |
| site:hackinglethani.com inurl:admin inurl:uselist | Search for user lists. |
Google is undoubtedly a powerful tool that can be very useful when performing an audit.
Lethani.


Amazing. That´s what I was looking. Great job!