During the last decade, the deep web has become very well known, everyone has talked about it. And the problem with this fame is that a lot of urban myths have arisen about this part of the Internet.
The deep web is the name given to all content that is not included in search engines. Without going into details about why a person would want to access the deep web, in this blog I’m going to show you how to connect using the Tor browser.
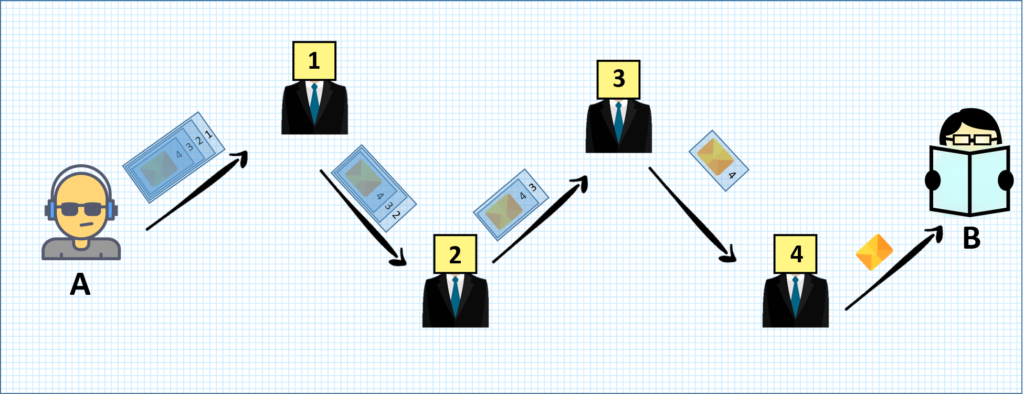
Tor is a browser that allows anonymous access to the Internet, thanks to its Onion Routing system. In a normal Internet connection, routing is direct: it is established from point A to point B. However, this is not the case with Onion Routing. In Onion Routing, to get from point A to point B, you first go through several random intermediate nodes.
Once you have chosen which nodes will act as intermediaries, A has to encrypt the message. To do this, it uses asymmetric encryption: it encrypts with the public keys of the intermediate nodes, starting with the last node and ending with the first. In this way, only the last node can see the message.
None of the intermediate nodes knows the origin or destination of the message. They also do not know what position they occupy in the network. These nodes are distributed all over the world, so anonymity is achieved. From time to time, usually about 10 minutes, A chooses new intermediate nodes again to establish its connection to B.
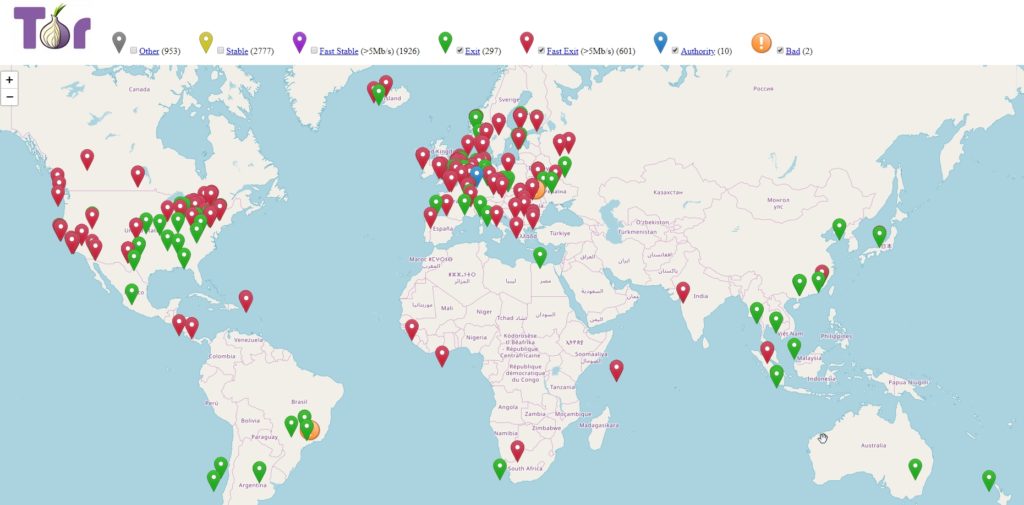
However, the network is not perfect. First of all, the last node can read the message, and the connection between this output node and the Internet is never encrypted, so if you do a man in the middle in the output node you will be able to get all the information. Intermediate nodes are resources ceded by anonymous people all over the planet. In TorMap we can see a map with all these nodes:
Anyone can deploy an intermediate node for use by other users. Therefore, a large organization that wants to take control of the Tor network would only have to deploy a large number of intermediate nodes to ensure that there is a high probability that its nodes will be chosen as intermediaries. If you have all the intermediate nodes, then you can find out where the message comes from and where it goes. This attack is known as the Sybil attack.
More complicated methods are also known to determine the origin of the message, based on statistics of size and frequency of messages received.
However, despite all these risks, the Tor network offers much more privacy and anonymity than a normal network, and can be used perfectly for legitimate purposes, and for surfing the normal network (in addition to deep web). So, here’s how to get in and surf using the Tor network.
Tor Browser
The first step is to download the browser from the official website and install it. The first time you open it, you will have to access the configuration. In some countries privacy is not very well regarded, and censorship prevails. In those cases, access via Tor is prohibited. However, the browser offers circumvention of this filter through the “pluggable transports” utility.
But of course, if Tor is censored in your country, you won’t be able to download it from the web. You can do this through https://gettor.torproject.org/, which offers the possibility of downloading via Twitter, email or using the XMPP protocol.
After downloading it, you can request the bridge nodes. You can also get them at bridges.torproject.org and put them in “Provide a bridge I know”.
Once set up, everything is ready to navigate. Now you can make a normal navigation, visiting pages that are in the superficial web, or visit the deep web. The deep web services that can be accessed through this browser end in .onion, and are made up of 16 alphanumeric characters.
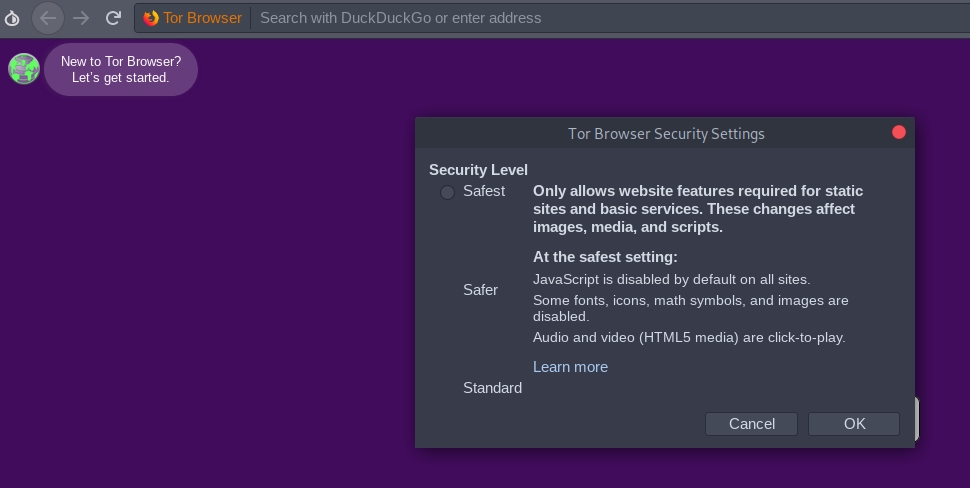
The first thing we must do is to configure the level of privacy and security that we want, clicking on the icon of the onion in the upper left corner. The “Standard” level gives us less security, but allows us to browse the network as we would with any browser. The “Safer” level deactivates JavaScript in webs that do not have HTTPS, as well as some fonts and mathematical symbols that are considered insecure. Finally, the “Safest” level only allows static web features, disabling javascript, fonts, icons and images from all sites, whether or not they have HTTPS.
Once we’ve done this, let’s go into the deep web. Let’s start with the onion service of the DuckDuckGo search engine (3g2upl4pq6kufc4m.onion). Using this search engine we can easily see which countries make up the Tor network we have formed to establish the connection:
In this case, we can see that from my IP (Spain) it connects to a node in France, from there to Germany, and from there to Canada. Then, it connects to 3 other nodes. If we look at the IP through which I’m going to the Internet with a page like www.iplocation.net, we can see that the final node is in Holland:
Finally, the page par excellence of the Deep Web through which to navigate to other .onion pages is the Hidden Wiki: http://zqktlwi4fecvo6ri.onion
In this page we can find all kinds of links, organized by sections.
This is the end of this post about privacy and anonymity with the Tor network.
Lethani.





Amazing
Hi, thanks for this, it was really useful for my thesis!