In this other post I talked about passwords and the conditions that must be met to be considered secure. However, if we enter the world’s strongest password on an insecure site, an attacker who has access to the database will be able to obtain it no matter how long or complicated it is.
The question then arises as to how to securely store the passwords of website users in a database. The answer is that the safest way to do this is not to save them. Instead, a reference to them, i.e. a hash, is stored. To understand this, let’s delve deeper into the concept of hash.
Hashes and Passwords
A hash is a one-way mathematical function. This means that from a password we can obtain a hash, but from a hash we cannot obtain a password.
In addition, a hash must comply with other rules:
- Two different passwords cannot generate the same hash (this phenomenon is called a collision).
- Two very similar passwords must generate completely different hashes.
- Must be deterministic: a password always generates the same hash.
There are several different functions for generating hashes, and some are safer than others.
Let’s take an example with the SSHA hash function:
- John’s pass is “love123” and it generates the hash {SSHA}vyQJOrcIff42xrwA+XNJZVFunZEvRpuz
- Ana’s password is “love124” and generates the hash {SSHA}WIeFElSf85FIn9RrAMSljMiKsDRseWAE
Returning to our problem, if we keep this password clear, and an attacker enters the database, he will discover that the password is “love123”. But if we don’t keep the passwords, we won’t be able to check if John is who he says he is.
However, if we save {SSHA}vyQJOrcIff42xrwA+XNJZVFunZEvRpuz, and an attacker gets this hash, he will still not know what John’s password is. And to verify that John is who he says he is, when he enters his password, the ssha(“love123”) hash will be calculated and this resulting hash will be contrasted with the one saved in the database: if they match, the password is correct.
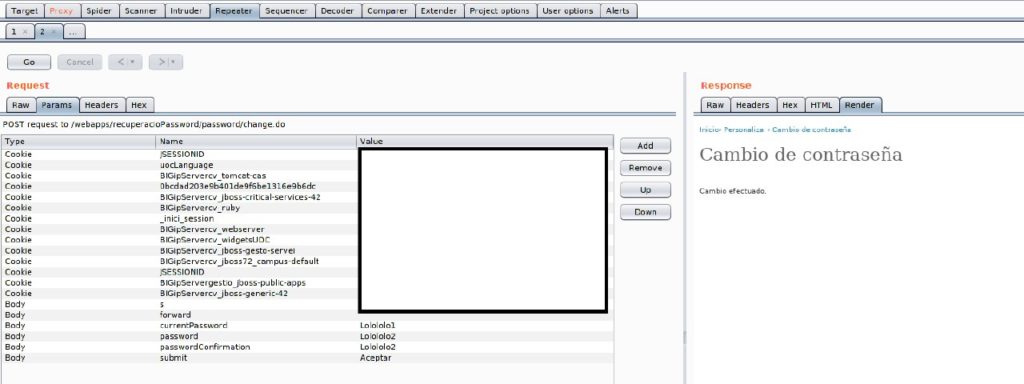
As an anecdote, some time ago I was alarmed because I wanted to change my password on the website of the cybersecurity master I’m doing, and I got the following message:
How is it possible that it indicated to me that the new password is similar to the current one? If you save the hash, a single character completely changes the hash output as we’ve seen before. The only possible option was to save the passwords in clear.
But before jumping to conclusions, I decided to pass the request through BurpSuite. And, to the great relief of all the students at this university, I could see that the validation was done locally with Javascript, since you also enter your current password, so it was just checking that the two fields of the form were similar. From Burp I could put two similar passwords and I had no problem:
How to brocken a hash: Hashcat
So much for the theory. Now let’s go hacking. One of the most used tools when breaking a hash is hashcat. The main options of this tool are:
- -m: Kind of hash to break. Hashcat can break several types of hashes, and depending on which is and the format in which it is, we must choose one mode or another..
- -n: Number of threads.
- -a: 0 for dictionary attack, 1 for combinations, 3 for brute force.
- -o: output file for save the results.
- -O: optimizes output.
- -S: saves progress in a session.
Brute Force
This type of attack is an attack by masks. Hashcat has a set of default rules, called masks, that indicate how the passwords we are going to generate are shaped. However, the most interesting thing is to create your own mask.
Each position of the mask can consist of a character or a character set. Hashcat defines 8 character sets:
- ?l : abcdefghijklmnopqrstuvwxyz
- ?u : ABCDEFGHIJKLMNOPQRSTUVWXYZ
- ?d : 0123456789
- ?h : 0123456789abcdef
- ?H : 0123456789ABCDEF
- ?s : !”#$%&'()*+,-./:;<=>?@[\]^_`{|}~
- ?a : ?l?u?d?s
- ?b : 0x00 – 0xff
In addition, we can manufacture up to 4 character sets of our own with the –custom-charset option. For example, putting –custom-charset1 ?d?l?u would indicate that by putting ?1 that character can be a number, a lowercase letter or a capital letter.
PoC
Let’s do a proof of concept. Imagine that you want to find out the Coca Cola formula, which can only be accessed by the company’s administrator. You’ve been planning the attack for months. You have been hired in the company, and you have been able to enter the machine of a foreman and you have obtained the hash of his password for access to the central server: 1ea9bda0289b5efa8e4a442a87d83d10. Through social engineering, you have used the shoulder surfing technique while the manager was writing his credentials, to discover that his password begins with P and another letter you have not seen, and the rest is a combination of 6 numbers that you have not been able to find out, but you know they are numbers because he used the numeric keypad.
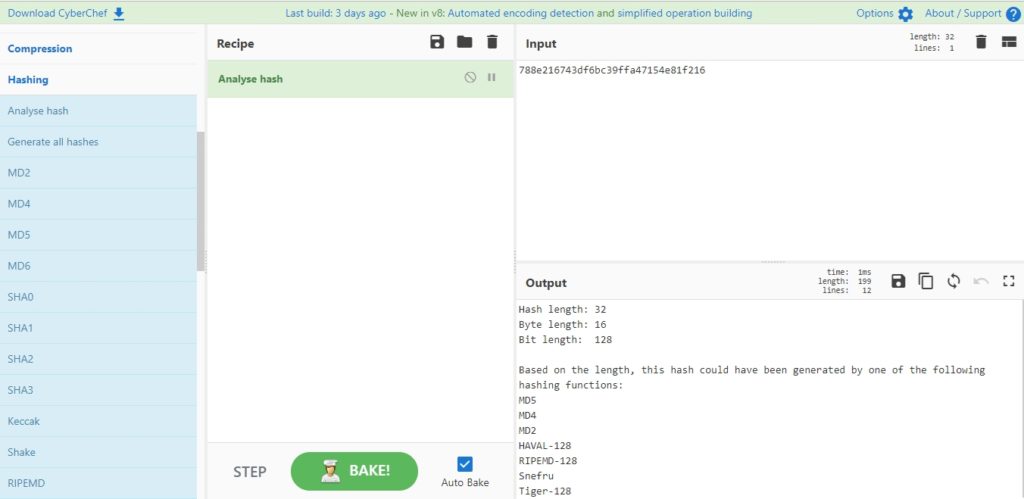
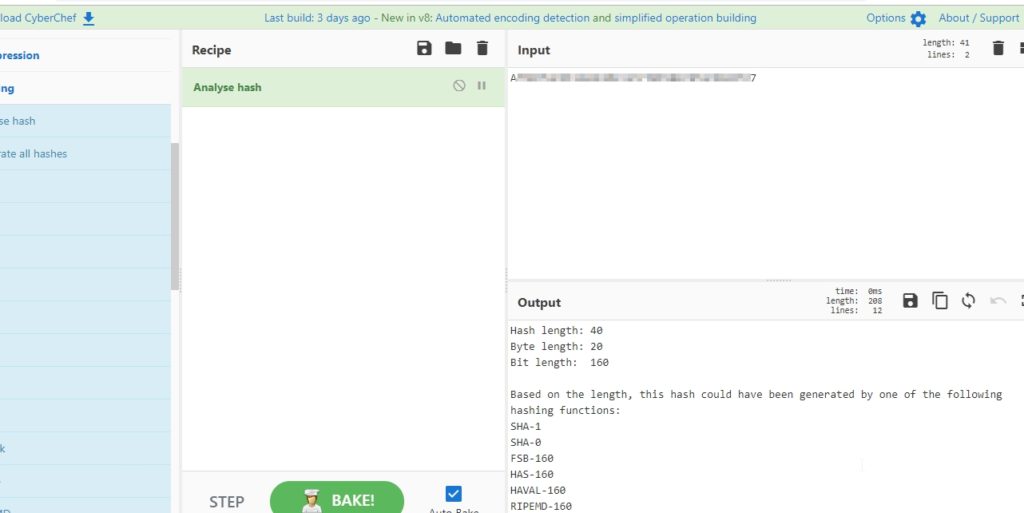
Well, the first thing we have to do is find out what kind of hash we have obtained. There are several ways to do this. One of them is to use CyberChef, with Hashing’s “Analyse Hash” option:
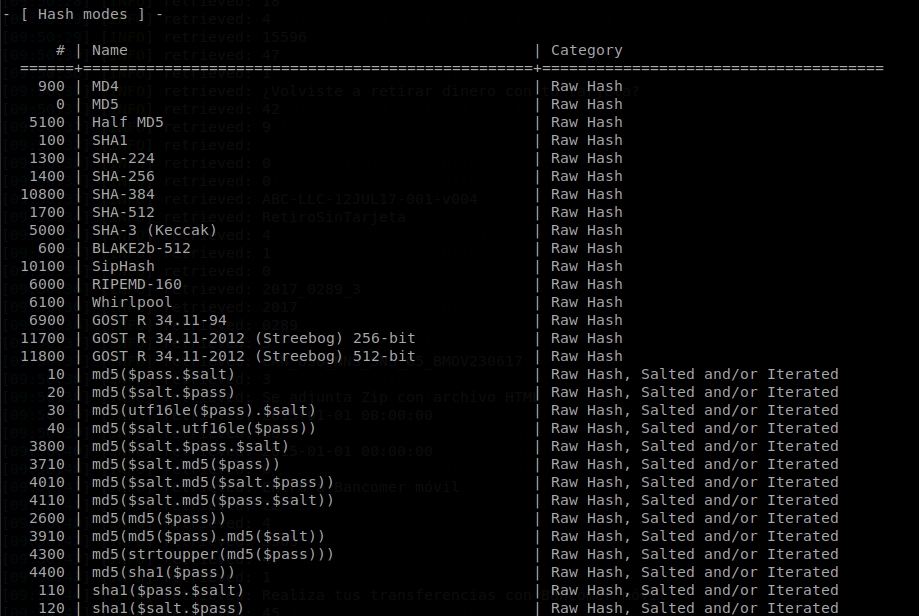
Looks like the hash is the MD5 type. To indicate it to hashcat, we make a hashcat –help and we see the different modes of execution that there are. In this case, the mode 0 is the one that corresponds to MD5, because we have the hash as it is:
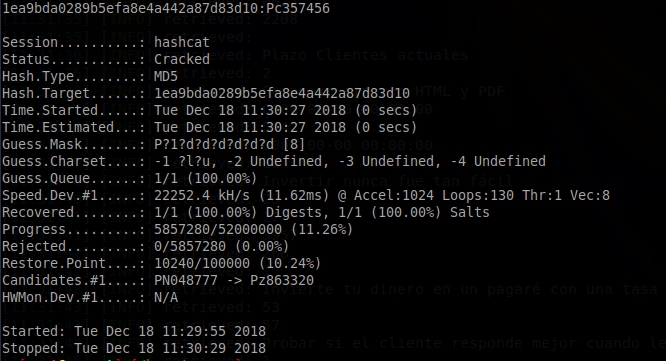
So the hashcat command would be hashcat -m 0 1ea9bda0289b5efa8e4a442a87d83d10 -a 3 –custom-charset1 ?l?u P?1?d?d?d?d?d?d?d?d?d?O (MD5 mode, the hash, brute-force attack type, ?1 is lower case or upper case, mask: first a P, then a capital or lower case, and then 6 numbers, optimized). Also, if you don’t have Intel OpenCL you should run the command with –force. We execute it, and in a few seconds we get the password:
The password is Pc357456. Now we can access the central server.
We have managed to access the central server, which gives us access to a web administration. However, the manager does not have enough privileges to access the file containing the Coca Cola formula. So you have explored the website for a while and discovered that through an SQL injection attack you can get the whole database. In the user table, you have found the administrator’s password, but again it is hashed.
When you check again in CyberChef what type of hash it is, you discover that it is SHA1 (I have decided to obfuscate the hash since it is a real password):
Esto son palabras mayores, ya no se trata de un simple MD5. Vamos a tener que personalizar más el comando de hashcat. Vamos a suponer que el administrador habrá utilizado una clave de entre 4 y 8 caracteres, que es lo más común. Por tanto, tenemos que añadir la opción –increment, para que vaya aumentando la longitud de las combinaciones, y la opción –increment-min=4, para que la longitud mínima sea 4. La máscara será ?a?a?a?a?a?a?a?a, puesto que entendemos que la clave de un administrador contendrá mayúsculas, minúsculas, números y símbolos (aunque lamentablemente para la seguridad de los sistemas, en muchas ocasiones no es así). Como es SHA1, utilizaremos el tipo 100, con el modo de fuerza bruta. De momento, el comando nos quedaría así:
These are big words, it’s no longer a simple MD5. We’re going to have to customize the hashcat command further. Let’s assume that the administrator has used a key between 4 and 8 characters, which is the most common. Therefore, we have to add the –increment option, to increase the length of the combinations, and the –increment-min=4 option, so that the minimum length is 4. The mask will be ?a?a?a?a?a?a?a?a, since we understand that the key of an administrator will contain capital letters, small letters, numbers and symbols (although unfortunately for the security of the systems, in many occasions it is not like that). As it is SHA1, we will use type 100, with brute force mode. For now, the command would look like this:
hashcat –increment –increment-min=4 -m 100 -a 3 hash.txt ?a?a?a?a?a?a?a?a
Let’s add some more parameters that can be useful to us. With -w we indicate how exhaustive it can be using resources of the computer or server where we are going to execute it, being 1 the lowest mode, and 4 the highest, that can cause that the desktop does not respond. We’ll put it at 3, high level. With -D we indicate the type of device that will use to crack the passwords. If we have a device with GPU, we will get better performance, so we can indicate options 1 and 2, to use both CPU and GPU. With -o we indicate the output file where you must save the cracked password.
Finally, since it is normal for a hashcat process to take hours or even days, we are going to take some precautions to safeguard ourselves from losing all progress if the process dies, or the connection to the server is lost, or the computer is shut down.
To do this, we will also execute the –session 1 parameter, which allows us to resume a session that has been aborted by saving it with the name “1”. In addition, I will use the nohup command, which assures us that the command that is written next will continue executing, even if the computer is blocked, and we will execute it in background putting an & at the end. We will add the command –status of hashcat, so that it automatically goes indicating the state.
And if for any reason we have to abort the process, then we can recover the progress using the hashcat command –status 1 –restore.
Finally, the command would look like this:
nohup hashcat –increment –increment-min=4 -m 100 -a 3 -w 3 -D 1,2 –session 1 -o dick hash.txt ?a?a?a?a?a?a?a?a –force –status &
The nohup command discards the input and adds the output of the command that is executed to ‘nohup.out‘. Therefore, we can make a tail -f nohup.out and will show us how the cracking goes, with the security that whatever happens will continue to run.
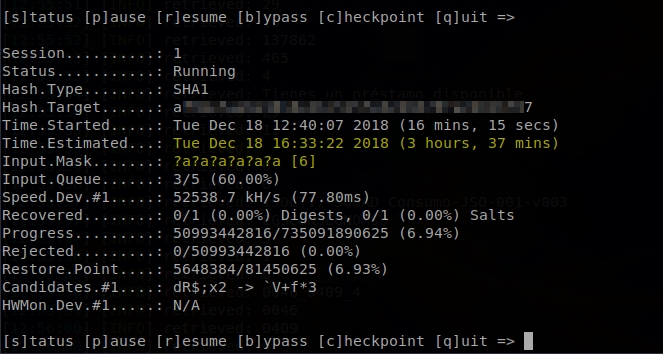
The most interesting thing about the status are the two lines I have highlighted in yellow. Input.Mask tells us that it is testing passwords of length 6. This means that it has tested all the combinations of the passwords of length 4 and 5 and has not found it. Time.Estimated indicates that it calculates that there are about 3 and a half hours left to finish with the length 6 passwords and start with the length 7 passwords.
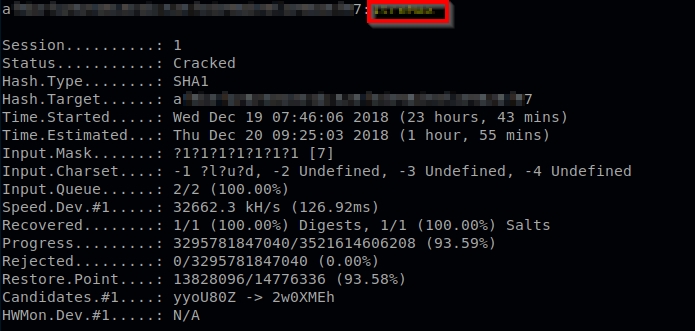
With patience and a powerful server, you can finally crack a SHA1 hash with hashcat:
We can finally find the Coca Cola formula!
Dictionary
In addition to brute force attacks, hashcat offers the option to perform dictionary attacks. This type of attack consists of introducing a list of words and go hash the corresponding of those words to see if in any case matches the hash we want to crack. If it matches, then that word is the one we are looking for.
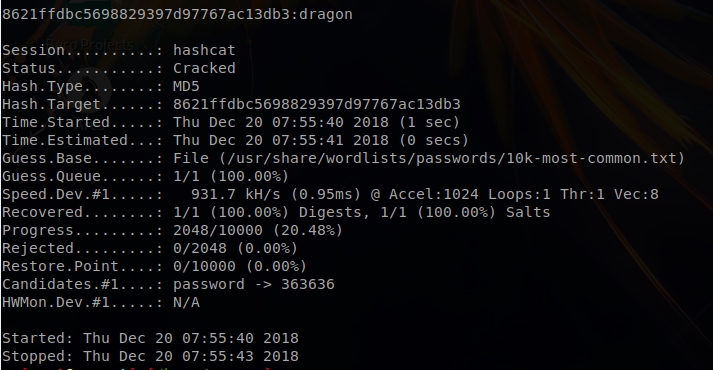
To do this, we only have to use the mode -a 0 and indicate the path of the dictionary. Let’s see a simple example with an MD5:
hashcat -m 0 -a 0 8621ffdbc5698829397d97767ac13db3 /usr/share/wordlists/passwords/10k-most-common.txt –force
The problem with dictionary attacks is that, if the word is not in the dictionary, the cracking attempt will fail, and if the dictionary is too long, the attack will take a long time.
There are other tools to perform brute force and dictionary attacks such as hydra or John the Ripper. In future posts I will make a comparison between these tools, showing similarities and differences.
Lethani.


1 thought on “The art of breaking a hash (Hashcat)”