On this post we are going to talk about how to get the most out of Remote Procedure Call, a protocol that is integrated in many applications. The “Remote Procedure Call” occurs when a computer requests a service that is on another computer and that goes over a network, without needing to know the details of that network, as all communications are encapsulated within this protocol.
In this way, programmers can execute these calls in the same way as they would if the code were on the same computer, calling remote processes as they would call local processes.
Typically, especially on windows, this service runs over SMB, port 139 and 445, as we can see below:
However, it usually has other ports open that show its presence, such as port 135, as we can see in the following nmap capture:
User Enumeration
Using the rpcclient we can obtain a lot of interesting information about the system and its users. Below we can see how it is possible to obtain the users of a Windows using the rpcclient command. Note that we have been able to access using an anonymous user (hence the inverted commas ‘ ‘ ) due to a bug in the privacy settings of this system.
Once in the rpc console, we execute the command enumdomusers to obtain the users of the domain as well as their relative identifiers (rid).
We can extend this information by using the querydispinfo command, obtaining the names and descriptions of the users.
Group Enumeration
By means of the command enumdomgroups we can see the different groups of users in the domain:
Of special interest is the Contractors group, as it is not one of the default groups. We can get more information about a group with the querygroup command, by specifying the group’s rid:
And through its rid we can also get the members of this group, using the querygroupmem command.
Other Commands
User SSID
Using the lookupnames command, we can obtain the Service Set Identifier (SSID) of a user.
The SSID is composed of the first part (everything up to the last dash) indicating the domain, and the second part (the last number) indicating the user.
The main thing here is that the administrator will always have the number 500 at the end of his SSID.
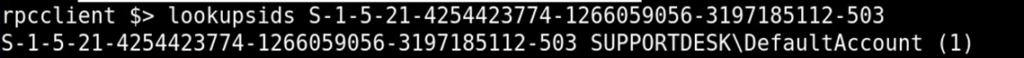
By looking at an SSID you can also see which user it belongs to, using the lookupsids command:
That is all for the moment about the RPC protocol. This protocol, although a priori it may seem harmless, can be the key to access a system thanks to the large amount of information it can reveal. On several occasions I have found windows computers running samba that a priori there was no way to attack, and thanks to rpcclient I was able to obtain the information I needed to break into them.
If you liked the article, I recommend you to visit the rest of the articles on infrastructure hacking.
Lethani.