We all know them. They plague our computers. But how are viruses made?
In general, talking about creating malware is rare in the area of cybersecurity, because unless you are dedicated to stopping it, there is no ethical reason why you should know how to develop malware.
Or is it? After all, a hacker seeks to push what he has in his hands to the limit. Well, today we have a Trojan horse. Let’s see how they do with a little PoC.
But first let’s review some important terms, so we don’t get lost before we start.
Terminology
Trojan: Malicious software that looks like a harmless program.
Modding: modify specific parts of the malware to make it undetectable. There are two types: binary modding, which consists in modifying an already compiled executable file, and modding source, which consists in modifying the source code.
Modding is taking antivirus signatures off the Trojans to make them undetectable. In a Trojan we have the malware part and the stub part (the part in charge of decrypting the encrypted malware, which travels with it).
Finally, with a crypter we will encrypt the Trojan. There are many crypters, and it is best to use the most up-to-date ones. Crypters can be found on pages and forums such as www.indetectables.net or www.underc0de.org.
Since to get an undetectable Trojan you have to do a lot of trial and error, being infecting a computer every time you want to test whether the Trojan works is a waste of time. To avoid this, it is first encrypted in a notebook (a program that when executed correctly simply saves a file with a text), and once we finish removing the signatures, then we do encrypt the Trojan. This works because when we remove the signatures we are modifying the stub, not the malware itself.
Metodology
Hexing: it is used to remove the most typical signatures that antivirus quickly detect. It is a manual and heavy method, and requires experience in malware. However, it’s the safest way to make it undetectable.
AvFucker: Automated and simple tool. We create a server, encrypt it, scan it, and when the antivirus doesn’t detect it, we pull out the signatures.
Dsplit: in case AvFucker detects all the files as infected, we use this program to remove signatures that we don’t get with AvFucker (this usually happens when using old crypters).
Alternative Dsplit: we will only use it if the previous two fail. However, it is best to use a more up-to-date crypter.
Offset not functional to functional: use it if after passing all the previous ones we still don’t get it or if the offsets are clean but don’t work when using them.
Change the stub: once we have the signature removed, we must change the stub of the crypter so that each time we use it it does not clean that signature.
These terms and tools may seem very intricate, but you’ll understand them much better in the PoC below.
Everything you need to work (except crypters) can be found in the Mooding Tools – MEGA PACK. Just google it and download it.
PoC: Trojan horse step by step
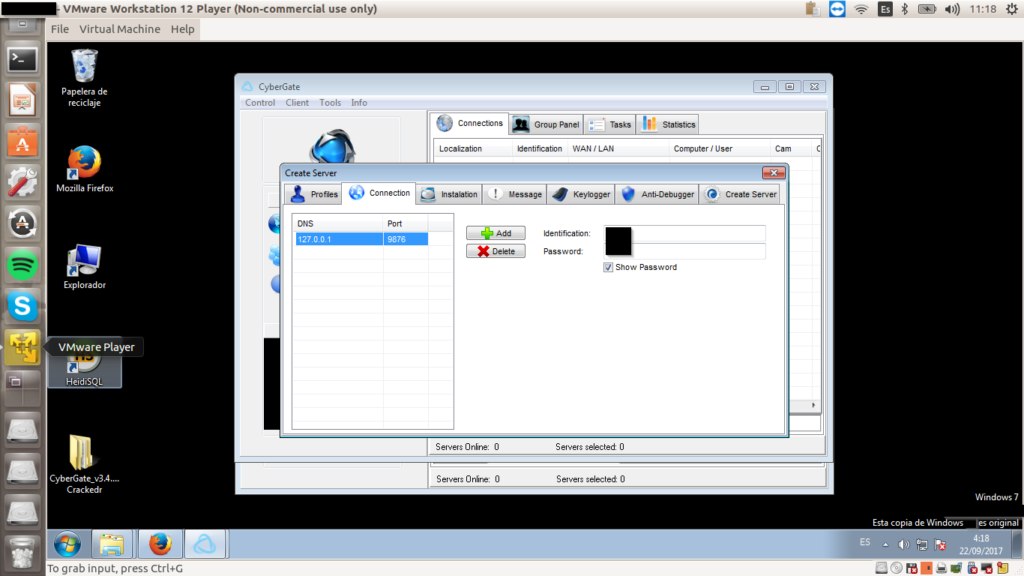
A Trojan is made up of a client (which will be on our computer listening) and a server, which is what we are going to put into the victim computer. To configure them, and to create a communication between the victim and our team, we will use the CyberGate program.
The first step is to self-infect, to find out what really works. So we must use a virtual machine with the victim’s operating system. For this PoC I’m going to pretend I want to infect a Windows 7.
We open CyberGate, create a new server, and put localhost in the DNS (127.0.0.0.1) because we want to infect ourselves to begin with. We choose a random port. It is important that it is not a common port. For example, 9876 will do.
There are some settings we need to make in this program. By activating the persistence and selecting the HKEY, we create a backdoor, and each time our victim computer is connected we can see it.
In “Message” we can show some message when the Trojan runs. This should only be done for testing purposes, because what is interesting is that the victim does not find out that he or she has a Trojan horse. We can also activate “Keylogger” to see everything the victim types.
Once the server is created (we will create a.exe with the name we have given, in my case server-copia.exe) we must go to the router and open the port 9876 (or the one you have chosen before).
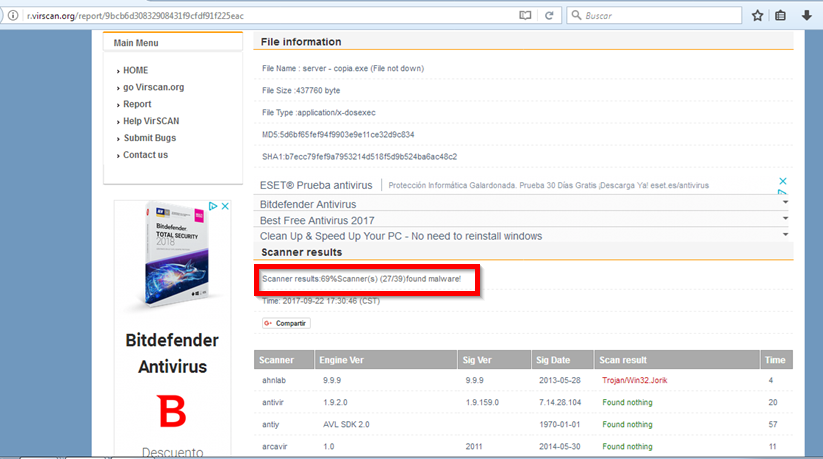
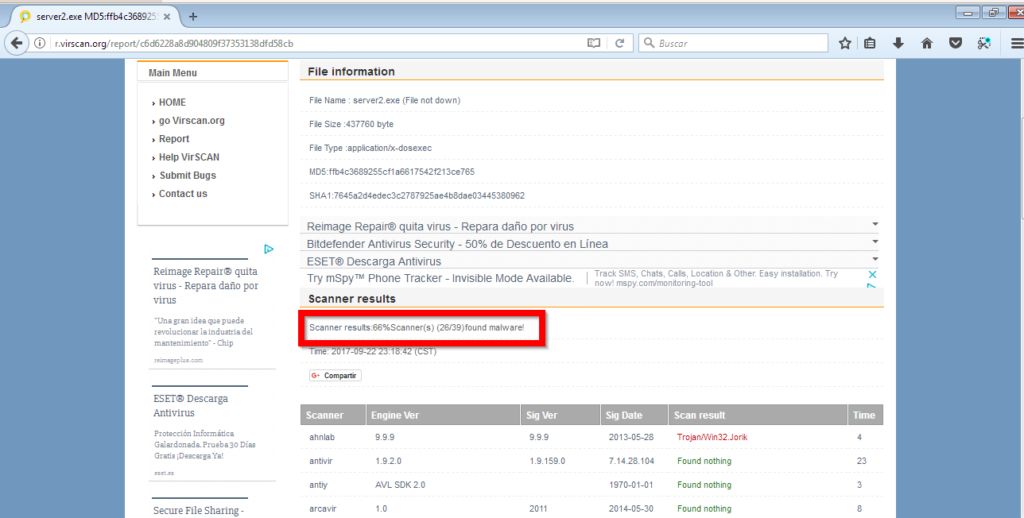
If we put it into the victim’s computer right now, most antivirus software would detect it. We can check this with a page that scans files for viruses. Important: do not do it in virustotal, since this page will communicate it to the antiviruses in case of finding malware (and would add the signature to them, cancelling our virus).
As we can see, crypter has only reduced the number of antiviruses that detect our virus by one. It’s still not enough. It’s Hexing time. We open a hexadecimal editor (no matter what, it can be IDA, Hex Editor, Hex Workshop… anyone) and proceed to delete any trace. To delete, we change the values to 0. What values to delete? there is no exact recipe, we must delete all kinds of tips such as “this program cannot be run in DOS mode”, “MSVBVMM60.DLL”, etc.
The idea is to gradually remove and check if the Trojan is still working. However, since this task is tedious enough, we can speed it up if instead of getting infected every time we want to try it, we use bookmarks. Encrypt the bookmark and hex on it instead of on the Trojan. Check how many antivirus programs detect it. And repeat. If the bookmark crashes, you’ve deleted something you shouldn’t have, go back to the previous version and try something else. And repeat. Your patience is the limit.
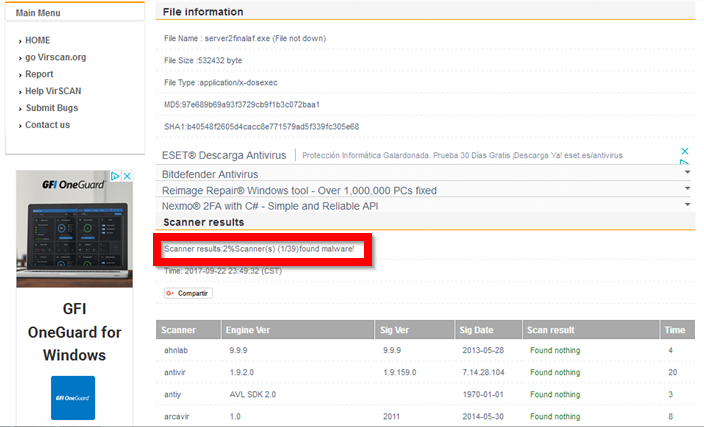
After this process, the number of antiviruses that detect our trojan has increased to 10:
Siguen siendo demasiados antivirus. Utilizaremos AvFucker para eliminar las firmas que quedan.
There are still too many antiviruses. We will use AvFucker to remove the remaining signatures.
Broadly speaking, AvFucker modifies the executable by creating thousands of very small (byte-level) variations, creating thousands of executables with different offsets. What we have to do is launch AvFucker by modifying the bytes from 1,000 to 1,000. The tool will detect the Final Offset (the initial one is 1,000). What it will do is fill everything with 90 (or whatever we choose), so that it doesn’t match the signatures on the antivirus files.
We download Avast, or any antivirus that offers the service of scanning offsets, and delete those that are infected. That way, only executables with offsets that have been transformed enough to not look like a virus will remain. In this case I was left with the offsets of 6,000 to 7,000 , and the offsets of 9,000 to 10,000.
We use AvFucker again, but now instead of going from 1,000 to 437,760 offset, we’re going from 6,000 to 10,000 offset, and instead of going from 1000 bytes to 1000 bytes, we go from 100 to 100 bytes. We generate the offsets, pass avast, and remove the infected ones. We repeat with the range that has remained, 1 in 1. And finally, the remaining executables have functional offsets free of avast signatures.
It is possible that altering the offsets may have altered the program and may not execute it properly. That’s why we have to keep trying until one of them runs, and we’ll already have a Trojan with a functional offset that evades all the antiviruses (except one, Panda has resisted me):
We could continue with more hexing or some other of the methods discussed at the beginning of this post, but for this first malware PoC I think it will be enough.
Now we only need to get the executable into the victim’s computer, which is usually done through social engineering, and when the victim runs it we will get all the victim’s information, including a remote desktop, a keylogger, users and passwords…
Finally, I remind you that using this information for evil purposes is worse than illegal: it is not from the Lethani. If you’re tempted, check your morals.
Lethani.





Hello, thank you for your tutorial. I have read and would like to test, but I can’t find a free crypter, connect-trojan is under maintenance. thank you for advising me.
Hello. And Bye.