This is the first post in the new section of the website where I will explain in detail a protocol in contrast and show examples of different ways to exploit different vulnerable implementations. To make these posts I have used as example implementations that can be found in the hackthebox.eu platform, as well as the Ippsec videos.
The File Transfer Protocol (FTP) is a network protocol for transferring files between systems connected to a TCP (Transmission Control Protocol) network, based on the client-server architecture.
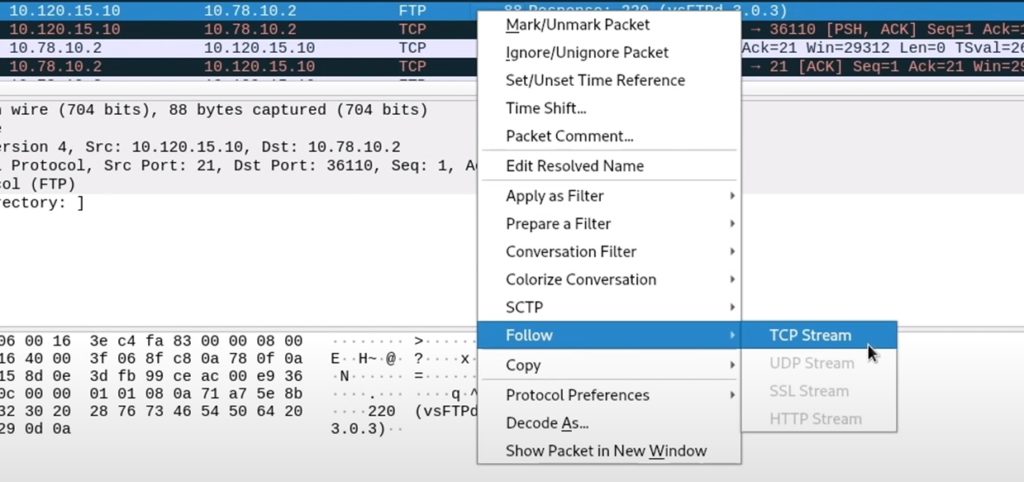
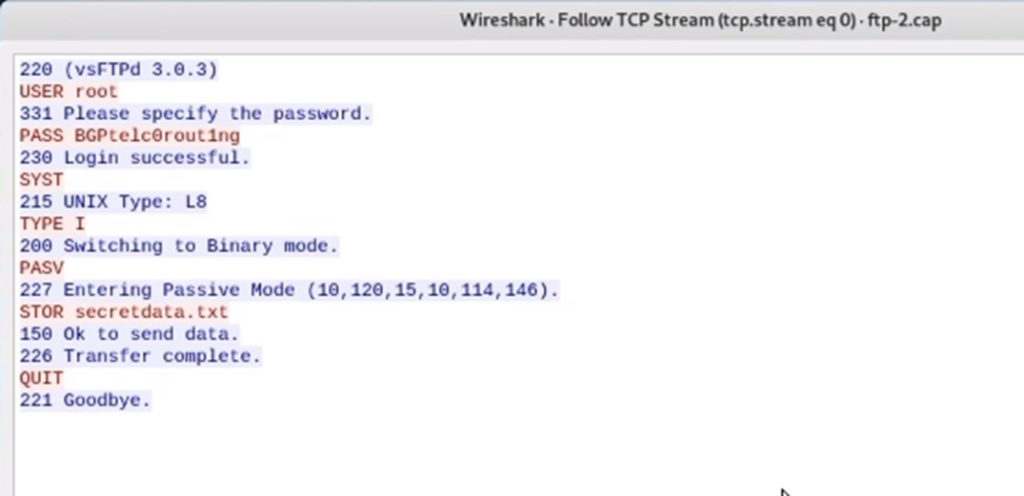
One of the characteristics of this protocol is that it is not encrypted. Therefore, if we obtain an FTP trace, we can open it with wireshark to see all the traffic, including the user and password:
Access
It is possible to access this service by indicating the host or IP and the port (default is port 21). For example, to access the ftp of this website (if you have it activated) you would only need to write on the terminal ftp hackinglethani.com
Anonymous Access
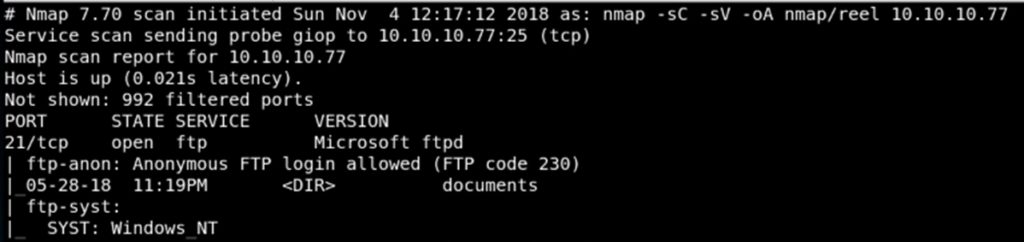
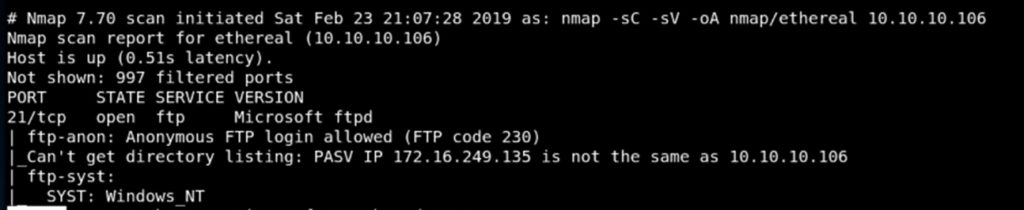
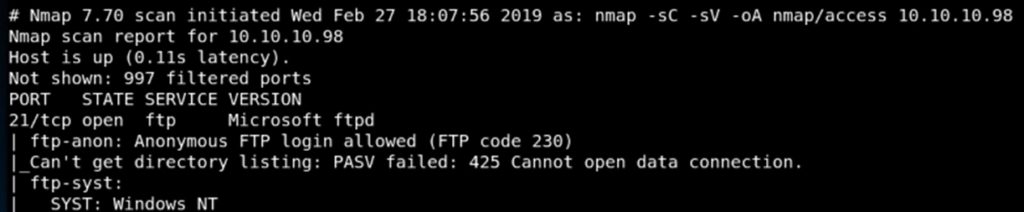
It is possible to access an ftp server anonymously if anonymous access is enabled. In the following image we can see how nmap reveals that anonymous access is active:
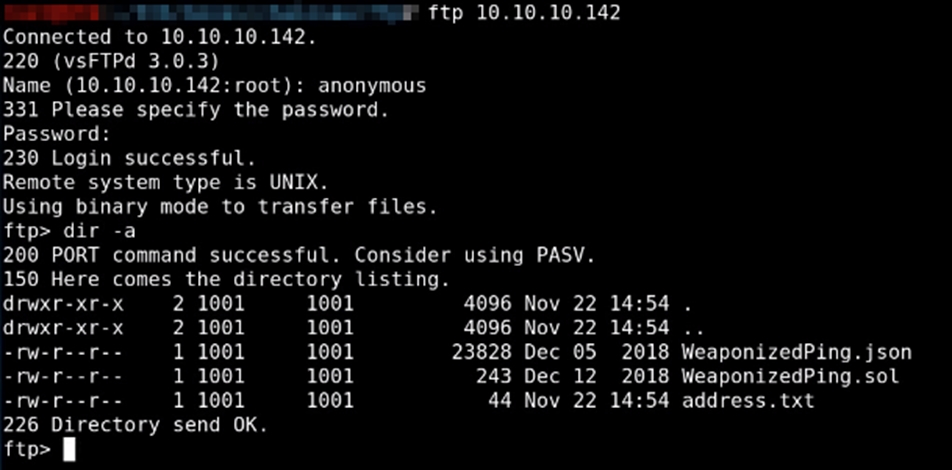
To access, you must enter “anonymous” and any password.
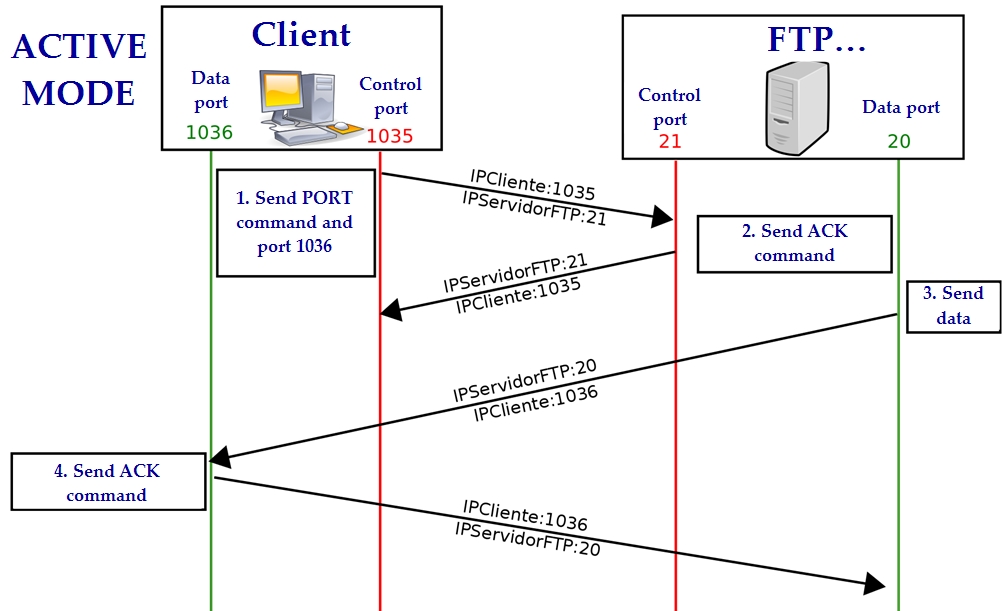
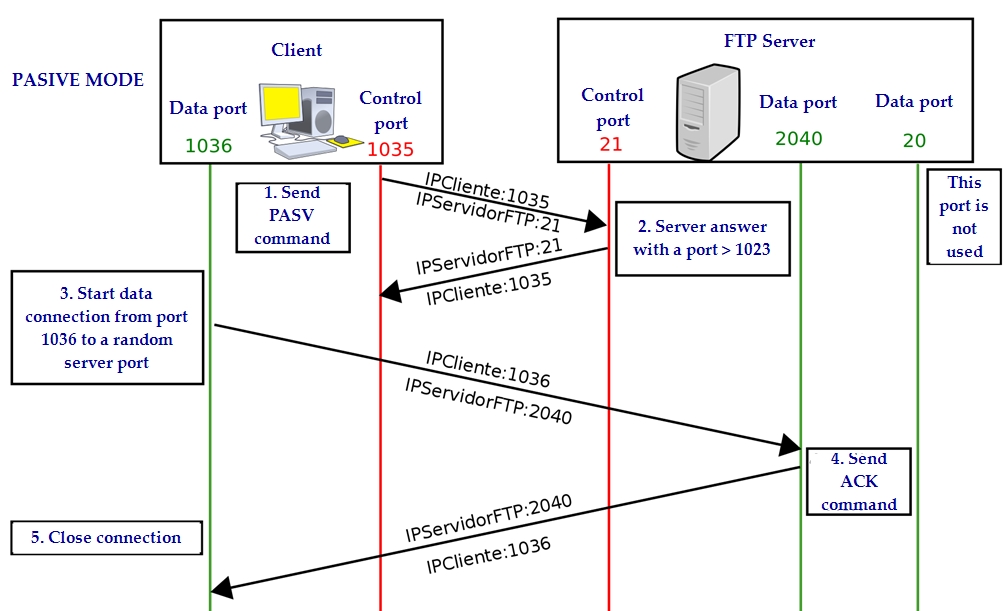
Connection modes
File Transfer
Ascii mode
To transfer files that contain only printable characters. You can modify line breaks and other file information.
Binary mode
To transfer binaries. The file is sent byte by byte without modification.
FTP Basic Commands
| ? | to request help or information about the FTP commands | |
|---|---|---|
| ascii | to set the mode of file transfer to ASCII (this is the default and transmits seven bits per character) | |
| binary | to set the mode of file transfer to binary (the binary mode transmits all eight bits per byte and thus provides less chance of a transmission error and must be used to transmit files other than ASCII files) | |
| bye | to exit the FTP environment (same as quit) | |
| cd | to change directory on the remote machine | |
| close | to terminate a connection with another computer | |
| close brubeck | closes the current FTP connection with brubeck, but still leaves you within the FTP environment. | |
| delete | to delete (remove) a file in the current remote directory (same as rm in UNIX) | |
| get | to copy one file from the remote machine to the local machine | |
| get ABC DEF | copies file ABC in the current remote directory to (or on top of) a file named DEF in your current local directory. | |
| get ABC | copies file ABC in the current remote directory to (or on top of) a file with the same name, ABC, in your current local directory. | |
| help | to request a list of all available FTP commands | |
| lcd | to change directory on your local machine (same as UNIX cd) | |
| ls | to list the names of the files in the current remote directory | |
| mkdir | to make a new directory within the current remote directory | |
| mget | to copy multiple files from the remote machine to the local machine; you are prompted for a y/n answer before transferring each file | |
| mget * | copies all the files in the current remote directory to your current local directory, using the same filenames. Notice the use of the wild card character, *. | |
| mput | to copy multiple files from the local machine to the remote machine; you are prompted for a y/n answer before transferring each file | |
| open | to open a connection with another computer | |
| open brubeck | opens a new FTP connection with brubeck; you must enter a username and password for a brubeck account (unless it is to be an anonymous connection). | |
| put | to copy one file from the local machine to the remote machine | |
| pwd | to find out the pathname of the current directory on the remote machine | |
| quit | to exit the FTP environment (same as bye) | |
| rmdir | to to remove (delete) a directory in the current remote directory | |
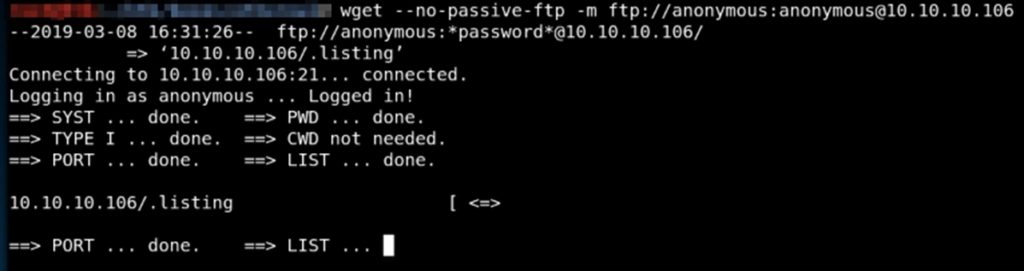
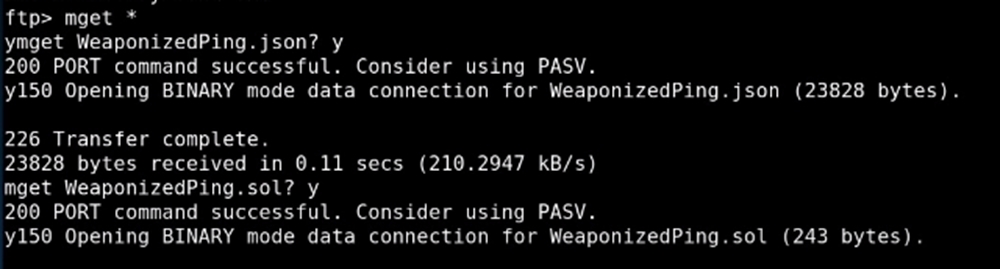
Multiple file download
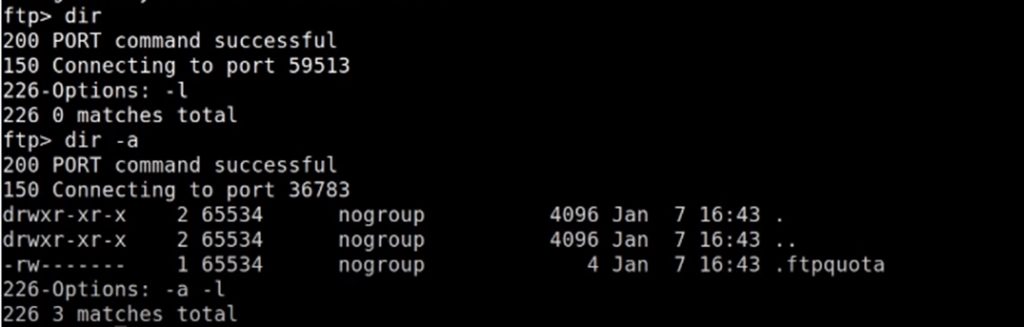
Listing hidden files
Local Server Time
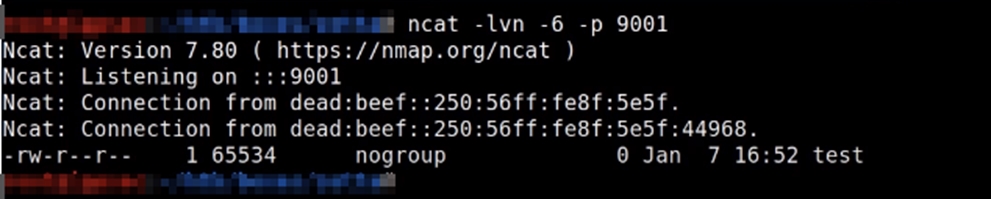
FTP via IPv6
However, we do not know the IPv6 address. To find out, we will use the vulnerability known as FTP Bounce Attack.
Let’s look at a server that allows FXP:
We can connect via netcat to execute FTP commands by typing them directly.
To do this we will use the EPRT command, as indicated by the RFC 2428:
Symlink
If, when the ? command is executed, the symlink option appears, perhaps we can create a symbolic link to the root directory.
symlink / test
By accessing /test on the website, we will be accessing the root directory of the server.
We can also see the content of php files, for example:
symlink /var/www/html/index.php /index.txt
FTP version
FTP vulnerable version: vsftpd 2.3.4
There is a version of FTP that is vulnerable, it has a backdoor. It is the version vsftpd 2.3.4
The vulnerability is that if you enter a smiley face 🙂 at the end of the username, you get command execution.
SSH Access
If we can create folders and upload files in a user’s home, we can create a .ssh folder, generate the RSA keys and connect to that user via ssh without knowing the password:
I hope you liked this first post where I showed you some of the most common ways to take advantage of the FTP protocol. In the next few weeks I will be uploading entries in which I will analyse the rest of the protocols.
Lethani.











I love reading through and I believe this website got some truly useful stuff on it! . Sibella Thorsten Silvano
Hello, I enjoy reading all of your article. I like to write a little comment to support you. Sonnie Arte Apfelstadt
Pretty! This has been an extremely wonderful post. Thank you for supplying these details.
Looking forward to reading more. Great post. Really Great.
Oh my goodness! Impressive article dude! Thank you
Very interesting post, I didn’t know that techniques, thank you!!